As a business leader, you don't manage IT systems; you manage risk. Cybersecurity is no longer an "IT problem"—it is one of the most significant financial, operational, and reputational risks your company faces. Yet, many business leaders are unprepared, believing they are too small to be a target. This is a dangerously false assumption.
We created this playbook to translate the complex NIST Cybersecurity Framework 2.0 into a clear, business-centric guide. Think of this less as a technical manual and more as a strategic briefing from your vCISO. We will explain what NIST is, why it's the gold standard for risk management, and how you can implement it to build a resilient, defensible, and more profitable organization.
The Financial Case: Quantifying the Staggering Risk for Growing Companies
A vCISO’s Take on NIST 2.0: Why the New ‘Govern’ Function is for You
The 6 Functions of Cyber Resilience (Translated for Business Leaders)
Beyond the Framework: NIST as a Compliance and Growth Enabler
How to Implement the NIST Framework in Your Company (Without Hiring a Full-Time CISO)
Frequently Asked Questions About the NIST Cybersecurity Framework 2.0
The Financial Case: Quantifying the Staggering Risk for Growing Companies
The belief that attackers only target large enterprises is an expensive misconception in the business world. In reality, your company is the ideal target because it is often the path of least resistance. Let's look at recent data.
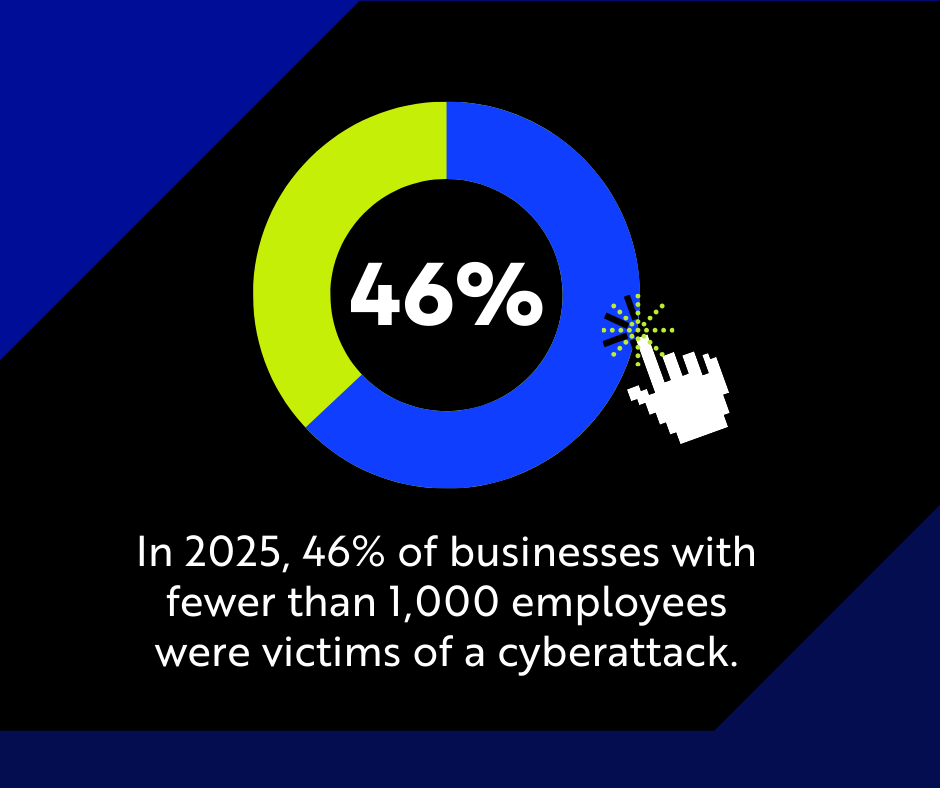
- You Are the Target: In 2025, 46% of businesses with fewer than 1,000 employees were victims of a cyberattack.
- The Ultimate Consequence: This is not a risk many businesses can survive. Authoritative reports from sources like the National Cybersecurity Alliance show that 60% of small businesses close their doors within six months of a significant cyberattack.
WHAT WOULD A RANSOMEWARE ATTACK COST YOU?
Use our calculator to calculate the potential cost of a ransom wear attack for your business.
This is why the NIST framework exists. It's not a set of rules; it's a strategic framework to prevent your business from becoming one of these statistics.
A vCISO’s Take on NIST 2.0: Why the New ‘Govern’ Function is for You
In 2024, NIST released version 2.0 of the framework. The most important change was the addition of a new, foundational function: GOVERN. This change was made specifically for business leaders, not IT technicians.
The "Govern" function makes it clear that cybersecurity is not just an IT task, but a core component of corporate governance and enterprise risk management. It's the "G" in GRC (Governance, Risk, and Compliance). It ensures that your cybersecurity strategy:
- Aligns with your business goals, mission, and strategic objectives.
- Manages risk from a top-down, business-wide perspective.
- Establishes clear roles, responsibilities, and accountability—placing ultimate responsibility with senior leadership.
- Addresses supply chain risk, which is a massive blind spot for most companies.
When you work with a vCISO, this is where they’ll always start. We don't begin by asking about firewalls; we begin by asking about your strategic vision, crown jewels, and goals of your business. The "Govern" function is the playbook for that conversation.
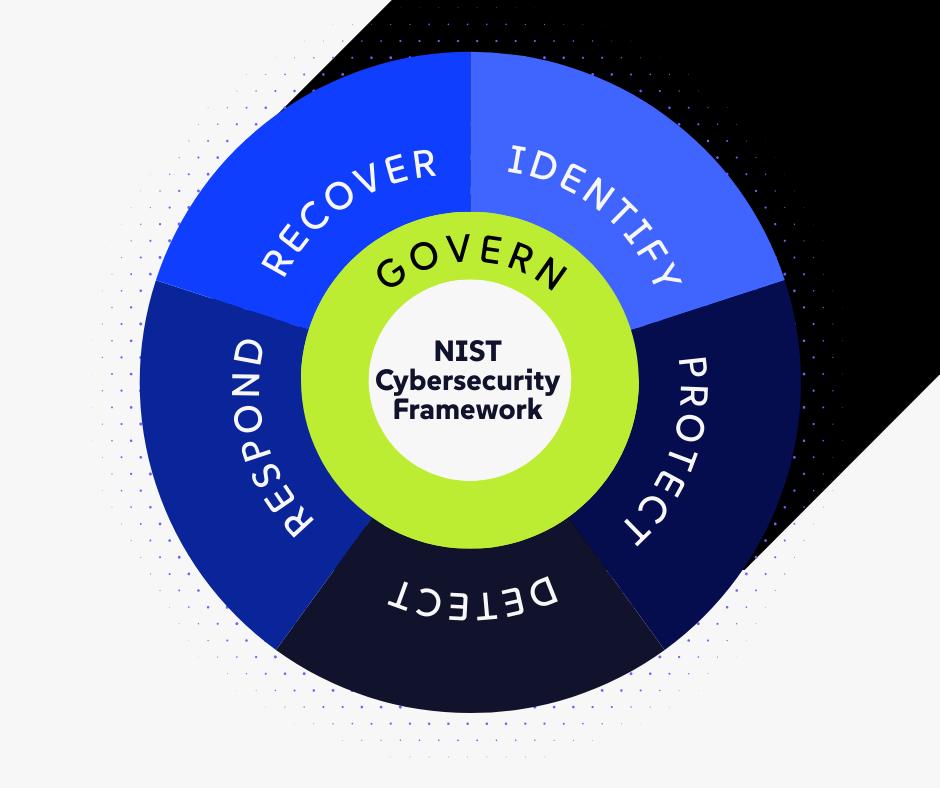
The 6 Functions of Cyber Resilience (Translated for Business Leaders)
The NIST CSF 2.0 is now built on six core functions. As a vCISO, I translate these from technical jargon into six simple business questions. A mature organization can answer all of them.
1. GOVERN: "Who is in Charge and What is Our Strategy?"
This is the new foundation. This function is about establishing and communicating your company's cybersecurity risk management strategy, expectations, and policies. It's the leadership-level "why" that drives all other technical "whats." It's where we create the policies, document the risks, and assign the executive-level responsibility to manage them.
2. IDENTIFY: "What Do We Need to Protect?"
You cannot protect what you do not know you have. This function is about creating a comprehensive inventory of your "crown jewels"—the data, systems, and assets that your business runs on. From a business perspective, this means asking:
- What is our most sensitive data (client PII, financial records, intellectual property)?
- Where does it live? Who has access to it?
- What would be the financial impact if that data was stolen, encrypted, or destroyed?
- What is our risk?
3. PROTECT: "How Do We Defend Our Fortress?"
Protect is the "locks on the doors" function. It involves implementing the data safeguards to prevent an attack from succeeding. This is where your technology partners deploy critical controls, including:
- Identity and Access Management: Ensuring only the right people have access to the right data (e.g., Multi-Factor Authentication).
- Cybersecurity Awareness Training: Addressing the human element, given that the 2024 Verizon DBIR found the human element was a component in 74% of all breaches.
- Data Security: Protecting your data at rest and in transit through encryption.
- Protective Technology: The essential firewalls, endpoint protection, and network security that form your perimeter.
4. DETECT: "How Do We Know When We're Breached?"
No defense is 100% perfect. This function is about finding attackers the second they get in. The average "dwell time" (the time an attacker is inside your network before being caught) is unacceptably long. This function is the job of a 24/7/365 U.S.-Based Security Operations Center (SOC), which uses AI-driven tools to hunt for threats in real-time.
5. RESPOND: "What is Our Plan When the Alarm Rings?"
When a breach is detected, panic and chaos are your worst enemies. A "Respond" plan is a pre-staged playbook that dictates exactly who does what and when. This includes communications, containment, and forensics.
Having a tested Incident Response (IR) plan is one of the single biggest cost-saving measures you can take. According to IBM's 2024 data, companies with a tested IR plan saved an average of $1.49 million in breach costs compared to those without one.
6. RECOVER: "How Do We Get Back to Business Safely?"
This function is focused on resilience. After an attack is contained, how quickly can you restore normal business operations? This is more than just "IT backups." This is a Business Continuity Plan that ensures your critical functions (like payroll, client service, and production) can resume, minimizing costly downtime and protecting your revenue stream.
How to Implement the NIST Framework in Your Company (Without Hiring a Full-Time CISO)
This is precisely why vCISO (virtual CISO) services exist. You don't need a $250,000/year full-time executive; you need a strategic partner who can guide you through this process. At CompassMSP, our vCISO-led approach turns this framework into a manageable, multi-year strategy.
Step 1: Governance & Scoping (Your "Risk Profile")
We start with the Govern function. A vCISO's first job is to understand your business, your risk tolerance, and your regulatory needs (e.g., HIPAA, CMMC). We work with your leadership to create a "Target Profile" that defines what "good" looks like for you.
Step 2: Conduct a Gap Analysis (Where Are You Today?)
Next, we conduct a comprehensive risk assessment, using the Identify function. We compare your current state ("where you are") against your "Target Profile" ("where you need to be"). This produces a clear, prioritized list of gaps, translated from technical findings into business-risk statements.
Step 3: Create the Strategic Roadmap (How We Get There)
This is the core of the vCISO value. We deliver a multi-year strategic roadmap that outlines the projects, policies, and technologies needed to close those gaps—using the Protect, Detect, Respond, and Recover functions as our guide. This roadmap is prioritized by risk and aligned with your budget and prepare you for whats “On the Horizon”.
Step 4: Implement, Monitor, and Manage (The CompassMSP Integrated Approach)
This is where strategy becomes reality. CompassMSP is unique because we don't just advise—we execute.
- Our vCISO leads the Govern and Identify strategy.
- Our Managed IT Services team implements the Protect controls.
- Our 24/7 U.S.-Based SOC delivers the Detect and Respond functions.
- Our Cloud & Infrastructure team ensures your Recovery plans are robust.
This integrated model—combining national-scale resources with the personal service of a regional partner—is the most effective way for a growing company to adopt the NIST framework.
Beyond the Framework: NIST as a Compliance and Growth Enabler
Adopting the NIST CSF 2.0 isn't just about defense; it's a powerful business enabler. It provides a common foundation that makes it significantly easier to achieve and maintain compliance with other, stricter regulations.
- For Healthcare (HIPAA): The NIST CSF provides a detailed roadmap for meeting the HIPAA Security Rule. This is critical when the average healthcare breach costs $10.94 million, according to IBM's 2024 data.
- For Financial Services (SEC/NYDFS/FINRA): Regulators explicitly point to the NIST CSF as the "gold standard." For RIAs, insurance brokers, and professional services firms, NIST adoption is no longer optional—it's an expectation.
- For Manufacturing & Construction (CMMC): If your company is part of the Department of Defense (DoD) supply chain, you are required to comply with CMMC. The entire CMMC framework is built directly on the foundation of NIST SP 800-171.
Your Next Step: Download the Business Leader's Guide to NIST 2.0
This guide has provided the "why" and the "what." Your next step is to get the "how."
We break down the NIST Cybersecurity Framework in plain language so you can understand what actually matters for strengthening security, improving resilience, and making NIST compliance far easier to put into practice.
Ready to speak with a vCISO about your specific business risks? Contact our team for a no-obligation risk and maturity consultation.
Frequently Asked Questions About the NIST Cybersecurity Framework 2.0
-
What is the biggest change in NIST CSF 2.0?
The most significant change is the addition of the "Govern" function. This new pillar firmly places cybersecurity as a core leadership and enterprise risk management responsibility, not just an IT task. It emphasizes that a successful program requires top-down strategy, alignment with business goals, and senior leadership accountability.
-
Is the NIST Cybersecurity Framework mandatory for my business?
No, for most private-sector businesses, the NIST CSF is a voluntary framework. However, it is widely considered the "gold standard" for demonstrating reasonable security and due diligence. Many government contracts require it, and it is the foundation for mandatory frameworks like CMMC. Regulators (like the SEC) increasingly view it as the benchmark for compliance.
-
We're too small to be a target, so why do we need this?
This is the most dangerous myth in cybersecurity. Attackers prefer growing businesses because they are the easiest path to money. With 46% of businesses under 1,000 employees attacked last year and 60% closing within six months of a breach, being "too small" is not a defense; it's a massive liability.
-
What's the difference between NIST and compliance (like HIPAA or CMMC)?
This is an excellent question. Think of it this way:
- Compliance (HIPAA, CMMC): These are sets of rules you must follow, often tied to a specific type of data (e.g., health data). They tell you what you must protect.
- NIST Cybersecurity Framework: This is the playbook that tells you how to build a comprehensive program to protect everything. The NIST CSF is the strategic "how-to" guide that helps you achieve and maintain multiple compliance mandates simultaneously.
-
How much does it cost to implement the NIST framework?
This is not a one-time cost but a strategic, ongoing investment in risk management. The cost depends entirely on your "gap analysis"—the difference between where your security is today and where it needs to be. The more critical question is: what is the cost of not implementing it? When the average breach for a small company costs $3.31 million, a phased investment in a vCISO-led program delivers an undeniable ROI.
-
What is a vCISO and how do they help with NIST?
A vCISO (virtual Chief Information Security Officer) is a service that provides you with executive-level cybersecurity leadership on a fractional, subscription-based model. A vCISO partner like CompassMSP leads the "Govern" function, performs the "Identify" risk assessment, builds the strategic roadmap, and manages the entire implementation and monitoring process across all six functions.
-
How long does it take to implement the NIST CSF?
Adopting the NIST CSF is a journey, not a destination. You are never "done." A vCISO can typically perform the initial risk assessment and deliver a strategic roadmap within 60-90 days. The implementation of that roadmap is a multi-year process, with critical "high-risk" items being remediated in the first six months, followed by a long-term plan for continuous improvement.
-
Can we just use software to become NIST compliant?
No. Software and tools are critical components of the "Protect" and "Detect" functions, but they are not a strategy. The NIST framework is a risk management program that requires governance, policies, procedures, and human expertise (like employee training and incident response). Technology is what you buy; a vCISO-led program is how you manage it effectively.
-
What is the official NIST website?
The official home for the National Institute of Standards and Technology (NIST) is www.nist.gov. You can find the Cybersecurity Framework 2.0 and all related resources, including their "Small Business Quick-Start Guide," directly on their site. This is the primary, authoritative source.
-
How does CompassMSP's approach to NIST differ from other providers?
Most IT providers can only sell you the "Protect" tools. CompassMSP is a comprehensive, integrated partner. We combine vCISO-led strategic governance (the roadmap) with end-to-end managed IT services (the implementation) and a 24/7/365 U.S.-Based SOC (the detection and response). We offer the national scale of an enterprise provider with the personal, high-touch service of a regional partner, giving you a single, accountable firm to manage your entire technology and security strategy.