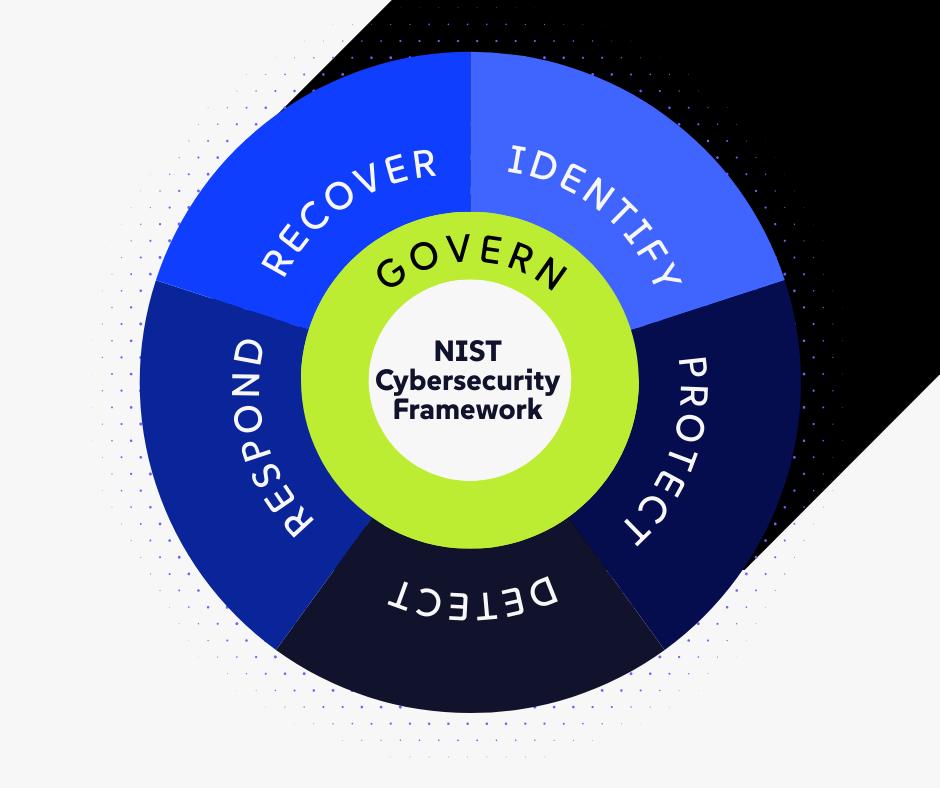
In our last guide, we discussed the Cybersecurity Risk Assessment, which fulfills the NIST Cybersecurity Framework's "Identify" function. That process is how we find your "crown jewels" and quantify the financial impact of their loss.
Now, we move from knowing the risk to acting on it.
Welcome to the "Protect" function.
From a vCISO's perspective, this is the most tangible part of your defense. It is the active, deliberate implementation of safeguards to ensure the delivery of your critical services. This isn't about buying a box and "setting it and forgetting it." It's about building a layered, 24/7 defense that makes it so difficult and expensive for an attacker that they move on to a softer target.
Treat this guide as your strategic investment plan. I will detail the 10 non-negotiable "Protect" controls and, more importantly, the business case for each.
What Is the NIST "Protect" Function? A Business Translation
The 10 Essential Controls for the "Protect" Function
How to Prioritize: A vCISO's 3-Phase Action Plan
Protection Isn't a "One-Time" Project, It's a Program
Frequently Asked Questions About the NIST "Protect" Controls
What Is the NIST "Protect" Function? A Business Translation
The official NIST definition for the "Protect" function is to "develop and implement appropriate safeguards to ensure delivery of critical infrastructure services."
Let's translate that from "gov-speak" into a business-first concept.
The "Protect" function is the collection of people, processes, and technology that serve as the fortress for your business. It is the "locks on the doors" and the "guards on the walls." It's designed to do one thing: prevent a cybersecurity event from becoming a catastrophic business disruption.
This function is where your vCISO's strategic roadmap (from the "Identify" phase) becomes a tactical, real-world defense.
The 10 Essential Controls for the "Protect" Function
These 10 controls are not "optional." In 2025, they represent the baseline for what regulators, clients, and insurance carriers consider "reasonable security."
A modern "Protect" strategy is a layered defense. Controls at the Perimeter (Firewall), Endpoint (EDR), Identity (MFA), and Human (Training) layers work together to protect your "crown jewels" (Data) at the center.
1. Multi-Factor Authentication (MFA)
- What It Is: The digital equivalent of needing both your key and your fingerprint to open a vault. It requires a user to present at least two pieces of evidence to log in—their password (something they know) and a code from their phone (something they have).
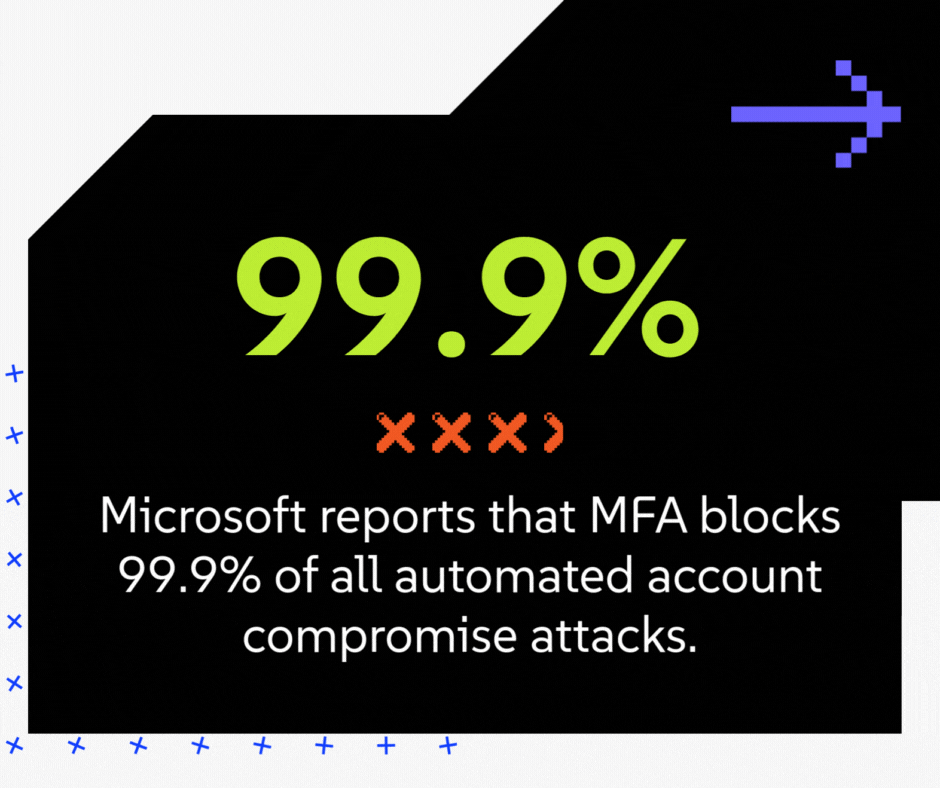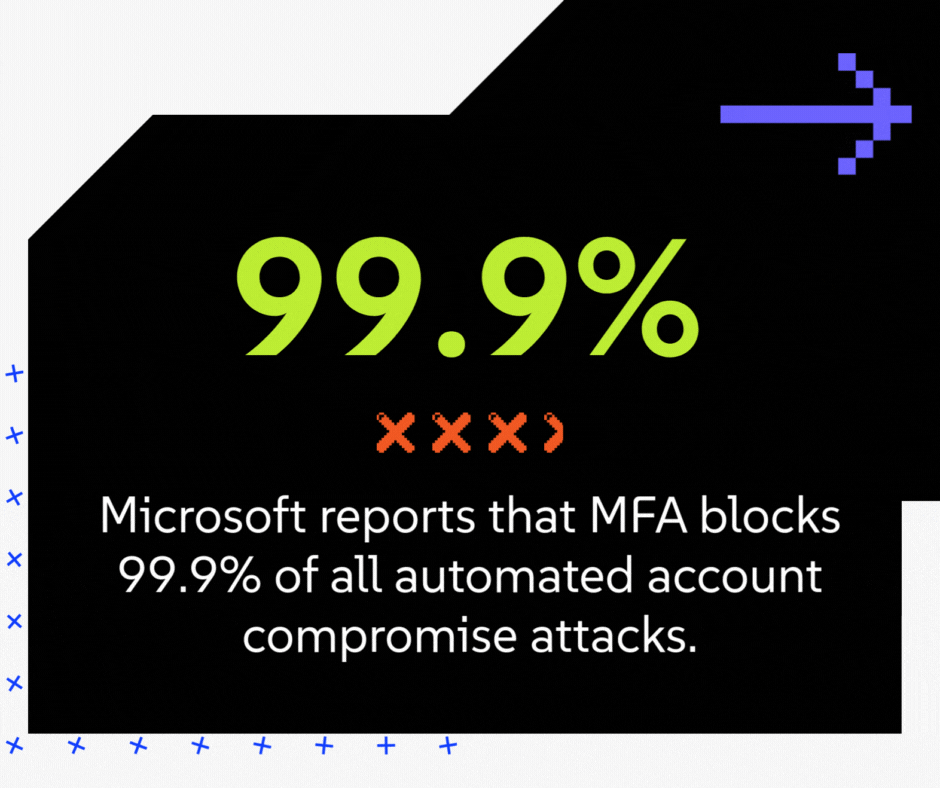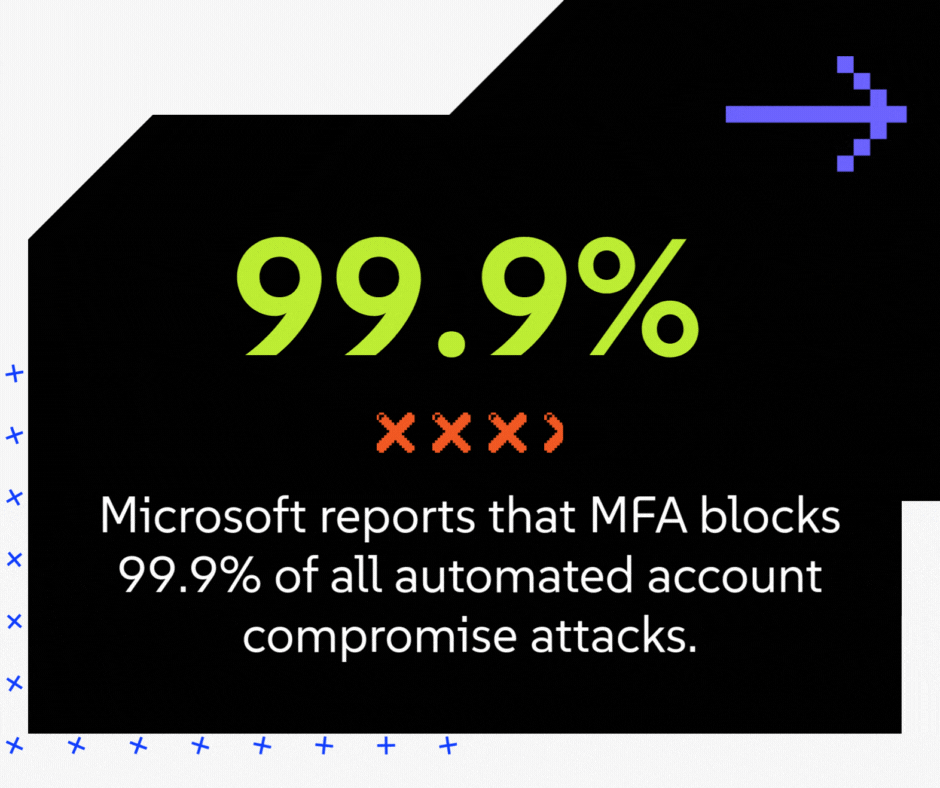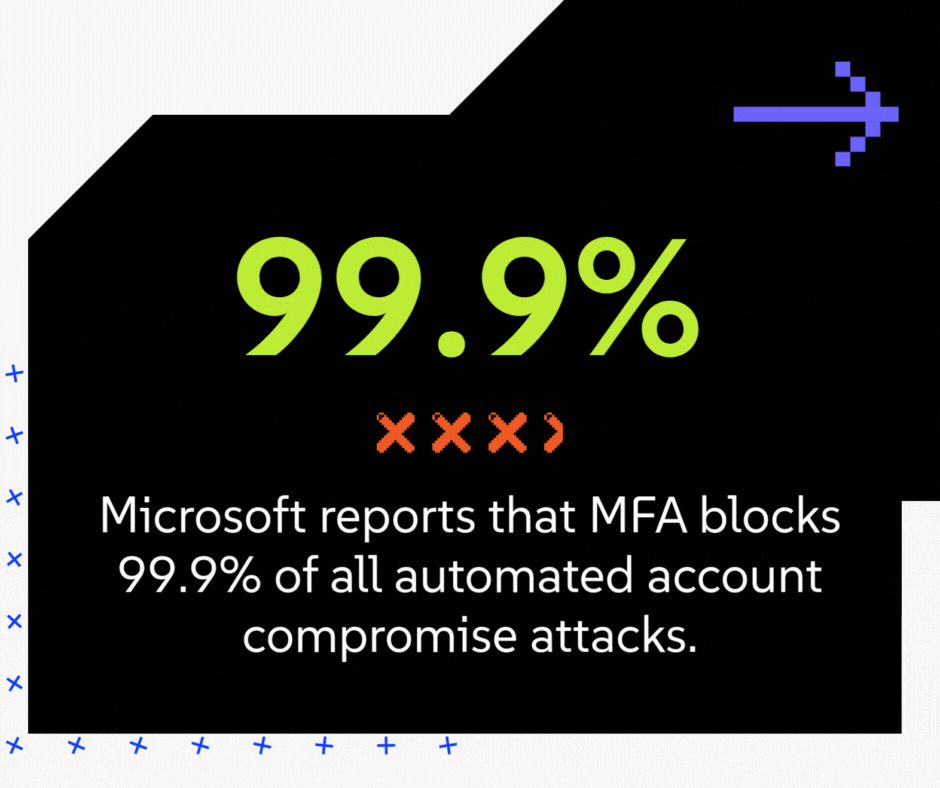
- The vCISO's Business Case: This is the single most effective, highest-ROI security control you can deploy. Microsoft reports that MFA blocks 99.9% of all automated account compromise attacks. A staggering number of breaches, including those that lead to fraudulent wire transfers, start with a simple stolen password. MFA makes the password useless to the attacker. From a CFO's perspective, MFA is your best defense against financial fraud from email compromise.
2. Advanced Endpoint Protection (EDR/XDR)
- What It Is: This is "antivirus" on steroids. Traditional antivirus looks for known threats. Endpoint Detection & Response (EDR) looks for malicious behavior. It assumes a threat might get in and watches for suspicious activity (like a Word doc trying to encrypt files), allowing it to stop zero-day and ransomware attacks that traditional AV misses.
- The vCISO's Business Case: The "endpoint" (your laptops, servers, and mobile devices) is the primary battleground. A 2024 report from the Ponemon Institute noted that 75% of organizations experienced one or more attacks that compromised an endpoint. EDR is the modern standard of protection. It's the difference between a silent alarm that's monitored 24/7 (EDR) and a "Beware of Dog" sign (traditional AV).
3. Continuous Security Awareness Training
- What It Is: A "human firewall." This is a continuous program, not a "one-and-done" yearly video. It combines computer-based training with regular, simulated phishing tests to teach your employees how to spot and report malicious emails.
- The vCISO's Business Case: The 2024 Verizon DBIR found the human element was a component in 74% of all breaches. Your people are your biggest attack surface. A well-trained employee, however, becomes a powerful security asset. This is a critical cost-control measure: CSO Online reports that phishing attacks cost businesses an average of $17,700 every minute. Training is an investment that provides a direct, measurable reduction in that risk.
4. Proactive Patch Management
- What It Is: This is the "digital maintenance" for your entire technology stack. When a software vendor (like Microsoft or Adobe) finds a security flaw, they release a "patch" (a fix). Proactive patch management is the process of testing and deploying these patches immediately.
- The vCISO's Business Case: Running unpatched software is like leaving a ground-floor window wide open with a sign on it. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) reports that 60% of all breaches in recent years involved an unpatched vulnerability. This isn't a "nice to have"; it's basic, mandatory hygiene. Automating this process via a managed services partner like CompassMSP removes the human error and ensures these "windows" are closed the moment a fix is available.
5. Next-Generation Firewalls (NGFW) & Network Segmentation
- What It Is: A "dumb" firewall just blocks or allows traffic from certain ports. A Next-Generation Firewall (NGFW) is an "smart" firewall. It inspects the content of the traffic to look for malware or malicious commands. Network Segmentation is the process of using that firewall to "micro-segment" your network, putting your critical servers (like finance) in their own secure "vault" that your workstations can't directly access.
- The vCISO's Business Case: Segmentation is a "containment" strategy. It prevents one compromised laptop from turning into a full-scale ransomware event that takes down your entire company. If an attacker breaches one workstation, they are "stuck" in that small segment, unable to see or access your "crown jewels." This contains the "blast radius" and turns a potential catastrophe into a minor, manageable incident.
6. Resilient, Tested Backups (with Offline/Immutable Copies)
- What It Is: This is your "get out of jail free" card for ransomware. A modern backup strategy involves the 3-2-1 rule (3 copies, 2 media, 1 off-site). Most critically, one of those copies must be "immutable" (it cannot be changed or deleted by anyone, including you or an attacker) or "offline" (physically disconnected).
- The vCISO's Business Case: A backup you have never tested is not a backup; it's a "hope." A tested backup is an asset. Gartner famously estimated the average cost of IT downtime at $5,600 per minute. In a ransomware attack, your RTO (Recovery Time Objective) is the difference between being down for four hours versus four weeks. A tested, immutable backup is the only way to guarantee a four-hour recovery.
7. Data Encryption (At-Rest & In-Transit)
- What It Is: This is the "digital safe" for your data. "In-Transit" encryption (like the "https" on your bank's website) protects data as it moves. "At-Rest" encryption (like BitLocker on your laptops) protects data on a hard drive. If a laptop is stolen, the thief gets a metal brick, not your client list.
- The vCISO's Business Case: This is a direct cost-control measure. In the event of a breach, encrypted data is often considered "unreadable" and may exempt you from certain breach-notification laws (particularly for HIPAA or NY DFS-compliant companies). This saves you millions in fines, legal fees, and reputational damage. The IBM 2024 Cost of a Data Breach Report noted that organizations with high levels of encryption adoption had an average breach cost $1.04 million less than those with low adoption.
8. Identity & Access Management (IAM) / Least Privilege
- What It Is: This is the business policy that dictates "who gets access to what." The "Principle of Least Privilege" is a core vCISO concept: every employee and system should only have the absolute minimum level of access they need to perform their job.
- The vCISO's Business Case: This control directly addresses the 74% human element risk. When an employee's account is inevitably compromised, the "blast radius" is limited by their permissions. If a new marketing coordinator has "Domain Admin" rights (a common lazy IT practice), an attacker who steals their password now has the keys to your entire kingdom. If they are properly restricted, the attacker is stuck in the marketing folder.
9. Cloud Security Posture Management (CSPM)
- What It Is: Your "cloud" (Microsoft 365, AWS, etc.) is just someone else's computer. A CSPM is an automated tool that scans your cloud environments 24/7 for misconfigurations (like a storage bucket set to "public") or non-compliance.
- The vCISO's Business Case: The "Shared Responsibility Model" means Microsoft secures their infrastructure, but you are responsible for securing your data and your configurations. Gartner famously projected that through 2025, 99% of all cloud security failures will be the customer's fault, primarily due to misconfiguration. A CSPM is the "locksmith" that ensures your new, complex cloud perimeter is secure.
10. 24/7/365 SOC Monitoring & Proactive Threat Hunting
- What It Is: This control almost bridges "Protect" and "Detect." A Security Operations Center (SOC) is a team of 24/7/365, U.S.-based security analysts who ingest all the logs from your firewalls, EDR, and cloud, using AI to look for the "faint signals" of an attack in progress. "Threat Hunting" is when those analysts proactively search your network for threats, assuming one is already in.
- The vCISO's Business Case: This is your alarm-monitoring service, your night watchman, and your forensics team, all in one. It’s what connects all the other 9 controls. The IBM report also found that organizations with security AI and automation (the core of a modern SOC) identified and contained breaches 108 days faster than those without. That 108-day difference is the difference between business survival and bankruptcy.
How to Prioritize: A vCISO's 3-Phase Action Plan
A list of 10 controls is not an action plan; it's a source of anxiety. You cannot and should not tackle all of these at once. As your vCISO, I implement these controls in three strategic phases.
| Phase & Focus | Timeframe | Strategic Goal | Key Controls |
|
Phase 1: The Non-Negotiable Foundation |
90-Day Sprint | Ensure Business Survival. Mitigate the most frequent and highest-impact threats (Human Error, Ransomware, Compromised Credentials). |
Control 1: Multi-Factor Authentication (MFA) Control 3: Continuous Security Awareness Training Control 6: Resilient, Tested Backups |
|
Phase 2: The Core Fortress |
6-Month Build-Out | Reduce "Blast Radius" & Containment. Build foundational controls that limit an attacker’s ability to move laterally and detect sophisticated threats. |
Control 2: Advanced Endpoint Protection (EDR) Control 4: Proactive Patch Management Control 5: Next-Generation Firewall & Segmentation |
|
Phase 3: Strategic Maturity |
12-Month Program | Achieve Programmatic Resilience. Implement advanced governance, data protection, and 24/7 visibility to move from a defensive posture to a truly resilient one. |
Control 8: Identity & Access Management (Least Privilege) Control 9: Cloud Security Posture Management (CSPM) Controls 7 & 10: Encryption & 24/7 SOC Monitoring |
Protection Isn't a "One-Time" Project; It's a Program
This list of 10 controls can be overwhelming. But the "Protect" function is not a one-time project; it's a continuous program.
This is the fundamental value of an integrated, vCISO-led security partner. You should not be in the business of vetting, buying, integrating, and monitoring 10 different security products. You are in the business of law, or manufacturing, or healthcare.
A mature security partner like CompassMSP provides the integrated stack:
- We Govern and Identify: Our vCISO builds the strategic roadmap and risk profile.
- We Protect: Our Managed IT Services and Security teams deploy and manage these 10 controls as a single, unified service.
- We Detect & Respond: Our 24/7/365 U.S.-based SOC monitors everything and executes the Incident Response plan
- We Recover: Our team manages the tested backups to ensure business continuity.
This model provides you with a national-scale security program, managed by an accountable partner, for a predictable, subscription-based cost. Then our cybersecurity report packages all ten controls into a comprehensive report to give you peace of mind and help you understand exactly where your organization stands. It's the only way to effectively and affordably implement the "Protect" function.
Your First 3 Actions
Feeling overwhelmed? Don't be. As your vCISO, I recommend you take these three, non-technical steps this week.
- MFA Audit: Ask your IT team/provider: "Is MFA enabled on every single cloud application, especially our email and financial systems? If not, I want a report on my desk by Friday with a plan to enable it."
- Phishing Test: Ask: "When was our last simulated phishing test, and what was the failure rate?" If the answer is "I don't know," schedule one.
- Backup Test: Ask: "When was our last full restore test from backup?" A "Certificate of Restore" is the only proof that your backup is a real asset.
Frequently Asked Questions About the NIST "Protect" Controls
-
What is the most important "Protect" control for my business?
Multi-Factor Authentication (MFA). It is not even a debate. It is inexpensive, easy to implement, and immediately neutralizes the most common and effective attack vector: stolen credentials. If you do nothing else on this list, do this first, as recommended in our "Phase 1" action plan.
-
What's the difference between the "Protect" and "Detect" functions?
Think of a bank vault. The "Protect" function is the 3-foot-thick steel door, the complex lock, and the reinforced concrete walls. Its job is to prevent someone from getting in. The "Detect" function is the motion sensor, the silent alarm, and the 24/7 camera feed. Its job is to know the instant someone is in and to catch them. You need both.
-
My data is in the cloud. Doesn't Microsoft/Google protect me?
No. This is the "Shared Responsibility Model." Your cloud provider (like Microsoft) is responsible for the security of the cloud (e.g., their data centers are secure). You are responsible for security in the cloud (e.g., your users, your configurations, your data). If you misconfigure a setting and leave your data public, that is your responsibility, not theirs.
-
We're a small business. Do we really need all 10 of these?
Yes. Your business has the exact same risk as a Fortune 500 company; you just have a smaller budget. An attacker uses the same automated tools to attack a 20-person company as a 20,000-person one. This is why you must partner with a managed security provider (MSSP) who can deliver these 10 controls at scale, giving you enterprise-grade protection for a cost-effective, multi-tenant price.
-
Isn't my old antivirus (AV) good enough?
No, not anymore. Traditional AV works by looking for "signatures" of known viruses. It's a list of bad-guys. Modern ransomware and zero-day attacks are brand new—they have no signature. Endpoint Detection and Response (EDR), the new standard, looks for bad behavior (like a program trying to encrypt your files), so it can stop new threats it has never seen before.
-
What is an "immutable" backup?
An immutable backup is one that, once written, cannot be changed or deleted for a set period. This is your ultimate defense against ransomware. Many modern ransomware strains will actively hunt for and delete your backups before they encrypt your files. An immutable backup cannot be deleted, ensuring you always have a clean copy to restore from.
-
How often should we really test our backups?
A backup that is not regularly tested is not a backup; it's a "hope." A full restore-test should be conducted at least annually, and file-level integrity checks should be run quarterly or even monthly. As your vCISO, I would require a "Certificate of Restore" from the IT team or managed partner every quarter.
-
What is the "Principle of Least Privilege?"
It's a simple, zero-cost security concept: People should only have access to the absolute minimum data and systems they need to do their job. A marketing intern should not be able to access the finance drive. A salesperson should not have administrative rights to their laptop. This policy contains the "blast radius" when an account is inevitably compromised.
-
How does a vCISO help with the "Protect" function?
The vCISO doesn't just hand you this list. They are the accountable executive who ensures this program is implemented, measured, and managed. The vCISO translates the Risk Assessment ("Identify") into a prioritized roadmap for these 10 controls (our "3-Phase Action Plan"). They then Govern the process, holding the IT team or managed provider accountable and reporting the progress (and your risk reduction) back to you and the board.
-
Which is more important: better tech (EDR) or better training (human)?
You must have both. They are two parts of a whole. The best EDR in the world can't stop an employee from being tricked into wiring $100,000 to a fraudulent account. And the best training can't stop a brand-new "zero-day" exploit. A vCISO-led program integrates the technical and the human, creating a layered defense where one control can catch what another one misses.