For many healthcare leaders, "cybersecurity" has long been synonymous with "HIPAA compliance." If the audit checklist is green, the assumption in the C-suite is that the organization is safe.
But the data tells a different, more alarming story.

Despite operating under some of the strictest regulatory standards in the world, the healthcare industry has suffered the highest average data breach costs of any sector for 14 consecutive years. In the most recent major study, the average cost of a single healthcare data breach hit a record $9.77 million.
This disparity reveals a dangerous truth: Compliance is mandatory, but it is not a shield.
HIPAA was written to ensure patient privacy. It was not built to stop a sophisticated ransomware cartel from encrypting your EMR (Electronic Medical Record) system in under 45 minutes. To protect patient safety and financial stability, healthcare organizations must move beyond the baseline of HIPAA and adopt the roadmap of the NIST Cybersecurity Framework (CSF).
HIPAA is the Baseline, Not the Ceiling
NIST CSF: The Roadmap to Resilience
At a Glance: HIPAA vs. NIST CSF
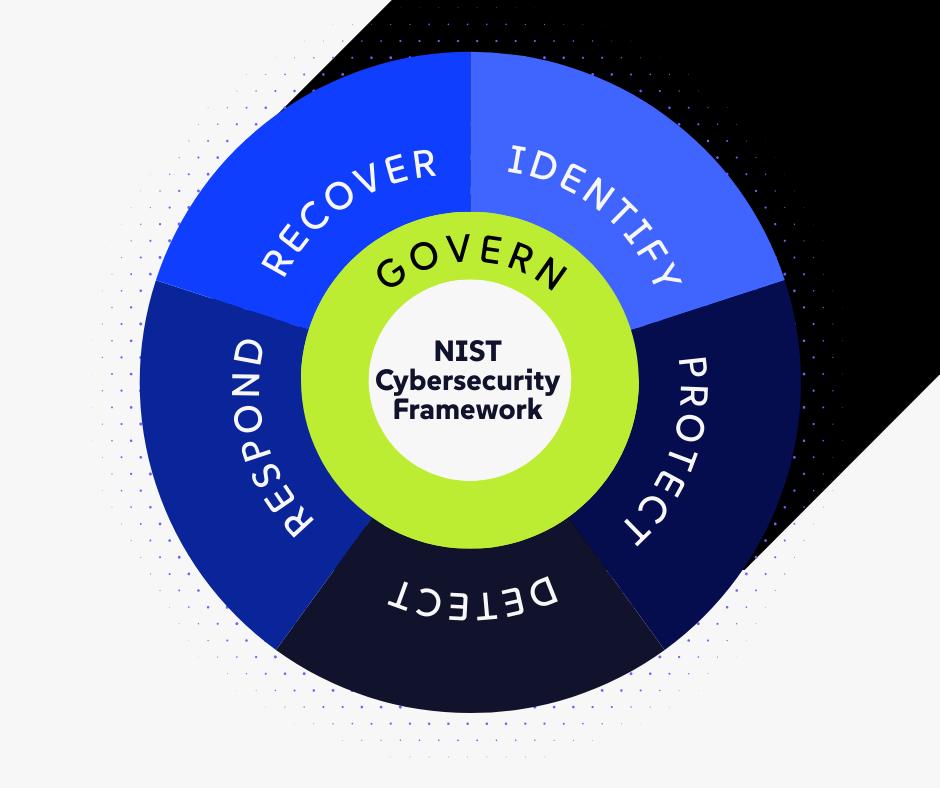
The Six Functions of Resilience
The 48-Hour Ransomware Test: A Tale of Two Hospitals
Why You Need Both HIPPA and NIST
Frequently Asked Questions: NIST vs. HIPAA Resilience
HIPAA is the Baseline, Not the Ceiling
To understand why HIPAA is failing to stop attacks, you have to look at its purpose. HIPAA’s Security Rule provides a list of standards—administrative, physical, and technical safeguards—that you must have.
Think of HIPAA as the building code. It ensures the doors have locks, the windows are sealed, and the fire exits are marked. It answers the question: "Are we following the rules?"
However, a building code does not tell you how to stop a determined intruder who knows how to pick the lock or break a window. It does not account for the speed of modern attacks or the complexity of connected medical devices.
Resilience, on the other hand, answers a different question: "Can we survive an attack?"
This is where NIST comes in.
NIST CSF: The Roadmap to Resilience
The National Institute of Standards and Technology (NIST) Cybersecurity Framework complements HIPAA but fills the critical strategic gaps. It shifts the organizational focus from "checking boxes" to "managing risk."
At a Glance: HIPAA vs. NIST CSF
|
The Security Challenge |
The HIPAA "Compliance" Approach |
The NIST "Resilience" Approach |
|
Risk Management |
Check the Box: Conduct an annual risk analysis to satisfy the auditor. |
Real-Time Visibility: Continuous monitoring of all assets, including "Shadow IT" and IoT devices. |
|
Access Control |
Policy Focused: Assign unique IDs and encourage strong passwords. |
Technically Enforced: Mandate Multi-Factor Authentication (MFA) and Zero Trust architecture for every user. |
|
Threat Detection |
Passive: Review audit logs monthly or quarterly to see who accessed data. |
Active: AI-driven tools hunt for threats 24/7 to stop attacks before encryption happens. |
|
Incident Response |
Process: Have a documented procedure for reporting breaches. |
Practice: Regular tabletop exercises and simulations to build muscle memory for the team. |
|
The Result |
You pass the audit, but may still be vulnerable to modern attacks. |
You pass the audit and survive the attack with minimal downtime. |
The Six Functions of Resilience
Here is how the NIST CSF transforms security in a hospital or clinical environment:
1. Govern: The Cultural Foundation
Introduced in NIST CSF 2.0, the Govern function is the most critical addition for leadership. It dictates how the organization’s risk management strategy is established, communicated, and monitored.
- The HIPAA Approach: Appoint a Security Officer.
- The NIST Approach: The Board reviews cyber risk metrics alongside financial and clinical quality metrics. Budgeting is aligned with risk tolerance, ensuring that security isn't underfunded compared to other operational needs.
2. Identify: Seeing the Invisible Risk
You cannot protect what you do not know you have, the Identify function helps you see what is invisible. Modern healthcare environments are flooded with "Shadow IT" and connected devices (IoT), from smart infusion pumps to Wi-Fi-enabled MRI machines.
- The HIPAA Approach: Maintain an inventory of hardware that stores ePHI.
- The NIST Approach: Map the entire data flow. This means identifying every connected device—including the HVAC system or the guest Wi-Fi—that could serve as a backdoor for hackers to reach the clinical network.
3. Protect: The Active Shield
The Protect function focuses on limiting the impact of a potential cybersecurity event. This is about safeguards that reduce the attack surface.
- The HIPAA Approach: Implement "unique user identification" and "emergency access procedures."
- The NIST Approach: Implement aggressive Identity and Access Management (IAM). This goes beyond passwords to include Multi-Factor Authentication (MFA) for every user, from the billing department to the ER doctors.
4. Detect: The Speed of Response
In the age of ransomware, speed is everything; that is where the Detect feature of NIST comes in. Hackers often dwell in a network for days or weeks before launching an attack.
- The HIPAA Approach: Implement "audit controls" and "examine activity."
- The NIST Approach: Continuous monitoring. This uses AI-driven tools to hunt for anomalies in real-time. If a receptionist’s account suddenly tries to access 5,000 patient records at 3:00 AM, NIST-aligned tools detect this behavior instantly.
5. Respond: The "Golden Hour"
When an incident occurs, chaos often follows. The Respond function ensures that the organization acts calmly and decisively to contain the damage.
- The HIPAA Approach: Have a "security incident procedures" policy.
- The NIST Approach: Practice the plan. This involves regular tabletop exercises where leadership simulates a breach. Who calls legal? Who calls the FBI? Who decides to shut down the network?
6. Recover: Clinical Continuity
Recovery is not just about restoring data; it is about restoring operations.
- The HIPAA Approach: Establish a "data backup and disaster recovery plan."
- The NIST Approach: Business Continuity. If the EMR is down for three weeks (the average ransomware downtime is over 20 days), how do doctors chart patients? NIST focuses on resilience—ensuring that clinical care continues even when the digital tools are gone.
The 48-Hour Ransomware Test: A Tale of Two Hospitals
Imagine two healthcare providers, Hospital A and Hospital B. Both are fully HIPAA compliant. Both pass their audits. But when a sophisticated ransomware gang strikes at 2:00 AM on a Saturday, their futures look very different.
Hospital A (The Compliance Focus)
- The Attack: Hackers exploit a vulnerability in an unpatched HVAC server. Because the audit only required checking medical devices, this server was overlooked.
- The Reaction: The attack isn't noticed until 6:00 AM when nurses can't access patient charts.
- The Outcome: The network is locked. Backups are found to be corrupted because they weren't tested frequently (HIPAA only requires a "plan"). Operations halt for 3 weeks. Patients are diverted. The cost: $10M+.
Hospital B (The NIST Focus)
- The Attack: Hackers try the same HVAC vulnerability.
- The Reaction: Identify: The asset map knew the HVAC server existed. Protect: Network segmentation prevented the hackers from jumping to the clinical network. Detect: AI tools flagged the unusual traffic instantly.
- The Outcome: The specific server is isolated automatically. Clinical operations continue without interruption. The cost: Zero downtime.
The Financial Case for NIST
For the CFO, the argument for NIST is purely financial. The gap between a "compliant" organization and a "resilient" one is measured in millions of dollars.
- Avoiding the $9.77 Million Hit
The average healthcare breach now costs $9.77 million. This figure includes technical remediation, legal fees, regulatory fines, and crucially, the cost of lost business.
- Lowering Insurance Premiums
Cyber insurance premiums have skyrocketed, but NIST offers a way to control them. Insurers favor NIST because it serves as proof of due diligence. Studies have shown that healthcare organizations adopting the NIST CSF have seen their cyber insurance premiums lowered by as much as 66% compared to those that do not.
Conclusion: You May Need Both HIPAA and NIST
This is not an "either/or" choice. You need HIPAA to remain legal. You need NIST to remain operational.
By mapping your HIPAA requirements to the NIST framework, you create a defense that satisfies the regulators and actually protects your patients. Don't settle for a passing audit grade. Aim for a secure future.
Frequently Asked Questions: NIST CSF in Healthcare
-
Is the NIST Cybersecurity Framework mandatory for healthcare providers?
Technically, no—but effectively, yes. While HIPAA is the only federal mandate for private healthcare organizations, the NIST CSF is increasingly required by cyber insurance providers, board governance committees, and business partners. If you want to qualify for lower insurance premiums or work with large hospital systems that demand rigorous third-party risk assessments, demonstrating alignment with NIST is often a non-negotiable requirement.
-
Does adopting NIST CSF mean we are automatically HIPAA compliant?
Not automatically, but it gets you 90% of the way there. HIPAA mandates what you must protect (ePHI), while NIST CSF provides the how. Because NIST is more comprehensive than HIPAA, an organization that fully implements the NIST framework will typically exceed the baseline requirements of the HIPAA Security Rule. There are official "crosswalk" documents available from HHS that show exactly how NIST controls map to HIPAA rules.
-
We already have a HITRUST certification. Do we need NIST too?
HITRUST and NIST are closely related. The HITRUST Common Security Framework (CSF) actually incorporates the NIST standards (along with ISO and HIPAA) into a unified control set. If you are HITRUST certified, you are likely already practicing the principles of NIST. However, using the simple language of NIST (Identify, Protect, Detect, Respond, Recover, Govern) is often better for communicating your strategy to the Board of Directors than the dense technical controls of HITRUST.
-
Will this increase our IT budget?
Initially, yes. Moving from "compliance" to "resilience" often requires investing in new tools (like active threat monitoring) and services (like a vCISO). However, this cost is a fraction of the alternative. With the average breach costing nearly $10 million, the ROI of avoiding a single incident can cover your NIST budget for decades. Additionally, many organizations see immediate savings through reduced cyber insurance premiums.
-
How does NIST handle "Shadow IT" and IoT devices?
This is one of NIST's strengths over HIPAA. The Identify function explicitly calls for a comprehensive inventory of all physical and software assets, not just those clearly marked as "medical devices." This helps organizations find and secure hidden vulnerabilities, like an unsecured smart thermostat or a physician’s personal tablet, that strictly compliance-focused audits often miss.
-
We are a small clinic, not a hospital. Is NIST too complex for us?
NIST is designed to be scalable. It uses "Implementation Tiers" that allow an organization to start small and mature over time. A small clinic might implement the "Protect" function differently than a major hospital (e.g., simpler firewalls vs. enterprise-grade segmentation), but the principle remains the same. Small businesses are prime targets for ransomware, making the framework just as vital for them as it is for large health systems.
-
How will I know if my company even needs NIST?
Cybersecurity is not a "one-size-fits-all" product. That's why we built a 2-minute quiz to help you determine if NIST compliance will be worth the investment for your company.