For the last five years, manufacturers in the Defense Industrial Base (DIB) have been hearing rumors, delays, and acronyms. "CMMC is coming." "It might change." "Just wait and see."
As your vCISO, I am here to tell you: The waiting period is over.
On November 10, 2025, the Department of Defense's (DoD) Final Rule for the Cybersecurity Maturity Model Certification (CMMC) officially took effect. If you manufacture parts, provide engineering services, or handle Controlled Unclassified Information (CUI) for the DoD, your ability to win or even bid on contracts now depends entirely on your cybersecurity score.
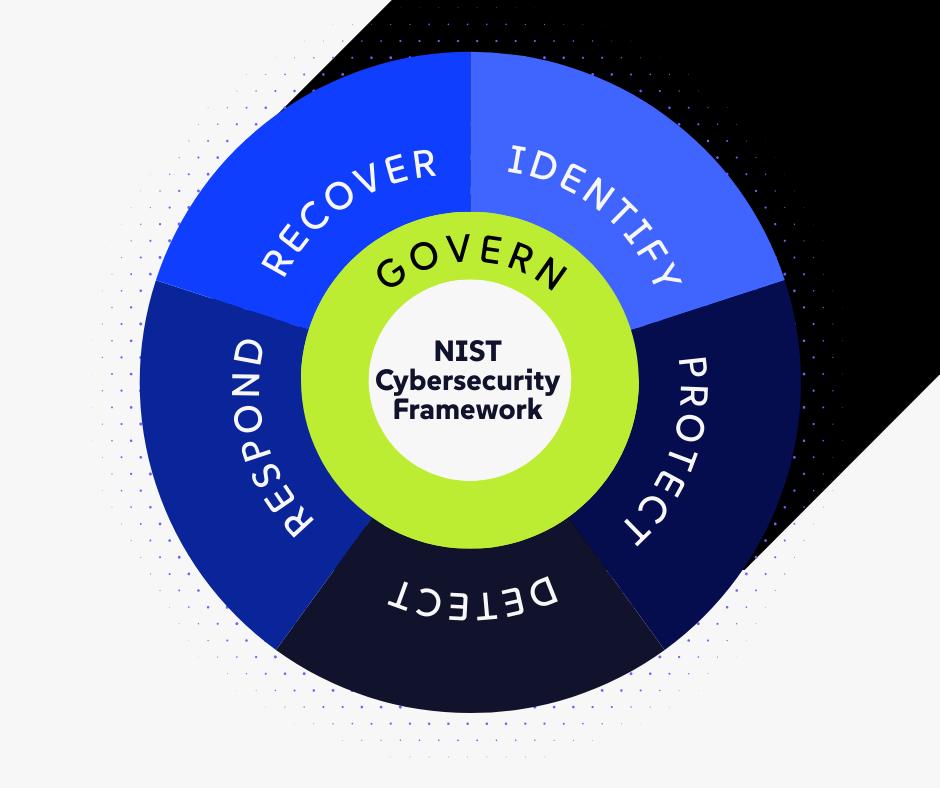
This article is not designed to induce panic; it’s to help you prepare. Specifically, it explains why the NIST Cybersecurity Framework (and its specific sibling, NIST SP 800-171) is the only roadmap that matters. If you master NIST, you master CMMC. If you ignore NIST, you risk losing your contracts and facing federal investigation.
The Core Link: NIST SP 800-171 Is the Test
Why Manufacturing is the Top Target (and the Cost of Failure)
3 Dangerous Security Myths in Manufacturing
The CMMC Timeline & The Attestor's Risk
How CompassMSP Gets Manufacturers "Audit-Ready"
Your Next Step: Know Your SPRS Score
The Core Link: NIST SP 800-171 Is the Test
Some manufacturing CEOs view CMMC as a "new" mysterious standard. It isn't.
CMMC Level 2, the level required for almost any manufacturer handling Controlled Unclassified Information (CUI) (blueprints, technical specs, CAD files), is simply a verification of a standard that has existed since 2017: NIST SP 800-171.
Think of it this way:
- NIST SP 800-171 is the textbook. It contains the 110 controls (the requirements) you must do.
- CMMC is the final exam. It is the auditor checking to see if you actually did the homework.
The vCISO Reality Check: If you are compliant with NIST SP 800-171 today, you are CMMC Level 2 ready. If you are not following NIST 800-171, you are already in breach of your current DFARS 7012 clauses, and CMMC will expose that gap to the DoD.
Why Manufacturing is the Top Target (and the Cost of Failure)
You might think, "I just make parts; why would foreign hackers target me?" They target you because you are the soft underbelly of the defense supply chain.
The data proves this is a targeted campaign against your industry.
The Bullseye:- For the fourth consecutive year, the Manufacturing sector remains highly exposed due to vulnerable systems and valuable IP. The primary method of entry is identity-based: Microsoft reports that over 99% of daily identity attacks are password-based, a critical weakness CMMC directly addresses with its Multi-Factor Authentication (MFA) requirements.
- The Dragos Q1 2025 Ransomware Report confirmed that manufacturing made up 68% of all industrial ransomware incidents.
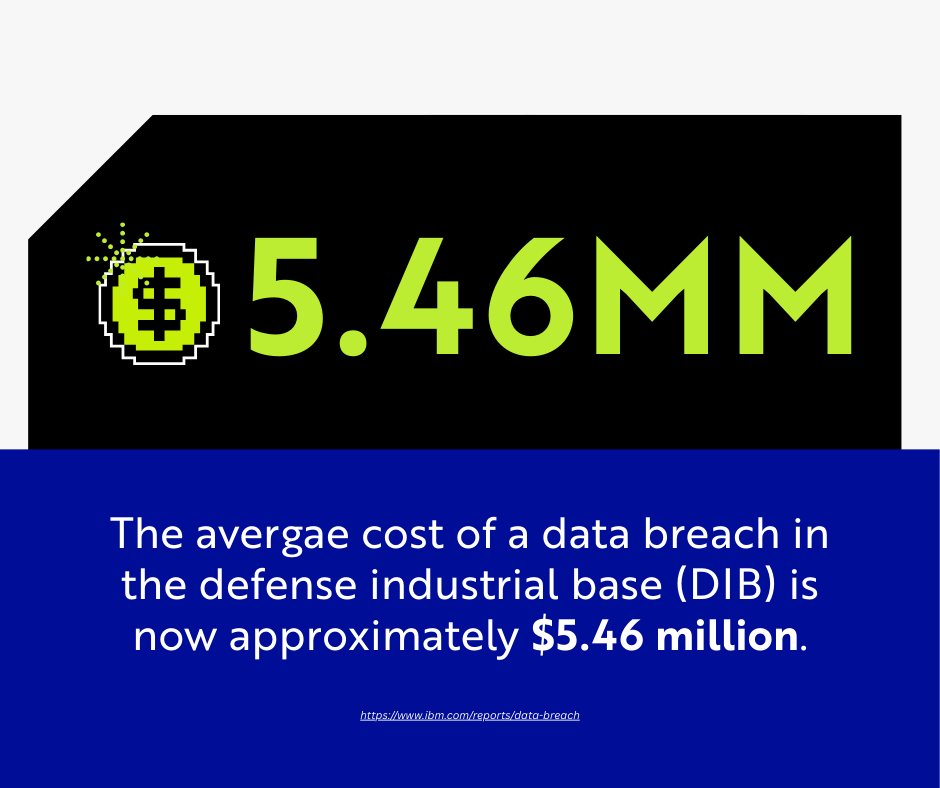
- The average cost of a data breach in the defense industrial base (DIB) is now approximately $5.46 million.
- Downtime from a cyberattack costs manufacturing companies an average of $260,000/hour.
CMMC is the DoD's mandate to stop their IP from being stolen through your network.
3 Dangerous Security Myths in Manufacturing
CMMC compliance starts with confronting the false assumptions that often plague the manufacturing environment.
1. Myth: "Our shop floor is air-gapped."
Reality: The air gap is a quaint relic. Modern systems—like remote diagnostics, employee cell phones connecting to the guest Wi-Fi, or technician laptops used for maintenance—have created digital bridges that destroy physical isolation. You must assume connectivity.
2. Myth: "We don't actually handle CUI, that's the prime contractor's job."
Reality: If you receive a technical drawing, a blueprint, or a performance specification, you are likely handling CUI. The requirement to protect it follows the data. Ignoring it is a violation.
3. Myth: "Windows XP/Legacy systems are safe because they aren't on the internet."
Reality: These systems become "specialized assets" that are CMMC's biggest challenge. They often run hard-coded credentials, cannot be patched, and become ideal vectors for malware carried in via USB drives during maintenance. They must be physically isolated and heavily monitored.
The CMMC Timeline & The Attestor's Risk
The "Final Rule" is effective right now. Here is what the phased rollout means for your firm, starting today:
Phase 1 (Active: Nov 10, 2025 – Nov 9, 2026)
- Requirement: Self-Assessments.
- What You Must Do: You must conduct a self-assessment against all 110 controls of NIST SP 800-171 and post your score to the DoD’s Supplier Performance Risk System (SPRS).
Warning: The Attestor's Signature is Personal Liability
Your company is required to have a senior corporate official attest to the accuracy of your SPRS score. Lying or guessing is a violation of the False Claims Act (FCA). FCA penalties can result in treble damages (3x the contract value) and personal civil penalties, turning a compliance issue into a massive legal disaster for the individual who signed the document. Your vCISO must validate this score before the signature.
How CompassMSP Gets Manufacturers "Audit-Ready"
We specialize in the manufacturing vertical. We know that you cannot shut down the shop floor to patch a server. Our vCISO-led approach is designed for operational reality.
Step 1: The SPRS Score Reality Check
We perform a mock assessment against the 110 NIST 800-171 controls to generate your real SPRS score. Most companies think they are a "90." We provide the objective score so you know the truth before the DoD does.
Step 2: Securing Legacy OT Systems (The Enclave Strategy)
This is the operational key to CMMC. Since you cannot patch legacy CNC systems, we employ isolation and compensating controls (Source 1.1).
- Isolation: We separate the CUI/OT network from your primary IT network using network segmentation (a strong NGFW).
- Compensating Controls: We apply all possible Access Control (AC) and Audit (AU) controls to the boundary. This means MFA on all remote connections (jump hosts) and 24/7 monitoring of the segmented network's gateway to catch any malware trying to bridge the gap.
Step 3: The System Security Plan (SSP) & POA&M
NIST 800-171 requires a written SSP. We author this strategic document for you, detailing how you meet every control. We then create a Plan of Action and Milestones (POA&M)—the strategic document that tells the DoD, "We know this gap exists, and here is our funded plan to fix it by Q2."
Your Next Step: Know Your Score
You cannot manage what you do not measure. The DoD requires you to have a score in the SPRS system today.
Do not guess. Let a vCISO validate your score so you can sign that contract with confidence. Schedule a CMMC Readiness Assessment.
Frequently Asked Questions about NIST for DoD Manufacturers
-
What happens if we fail a CMMC audit?
You lose the contract or become ineligible to bid on future contracts requiring that CMMC level. There is no probation period. If a solicitation requires CMMC Level 2 and you do not have the certification at the time of award, you are ineligible.
-
We use Microsoft 365 Commercial. Is that CMMC compliant?
No. Standard Microsoft 365 (Commercial) does not meet the strict requirements for data segregation and incident reporting required for handling CUI under DFARS. Most defense contractors need to migrate to Microsoft 365 GCC High, a sovereign government cloud. CompassMSP specializes in these migrations.
-
What is the biggest security gap in manufacturing today?
Identity and Access. The Microsoft Digital Defense Report 2024 indicates that 97% of identity attacks were simple password spray attacks. In manufacturing, these compromised accounts are often used to access high-value IP or to deploy ransomware into unsegmented networks. The foundation of CMMC is strong identity controls.
-
How long does it realistically take to get ready for CMMC Level 2?
The average time to move from "zero" to "CMMC Level 2 Ready" is 12 to 18 months. This timeframe includes gap analysis, technology deployment, documentation (writing the SSP), and the three-month period required to gather evidence for the auditor.
-
How will I know if my company needs NIST?
Cybersecurity is not a "one-size-fits-all" product. Just because NIST has great name recognition doesn’t mean it is the best framework for your specific business. That's why we built a 2-minute quiz to help you determine if NIST compliance will be worth the investment for your company.