The most dangerous phrase in financial regulation today is "Reasonable Security."
It is vague, subjective, and the primary standard the SEC, FINRA, and NYDFS now use to judge your firm. This marks a critical shift for CCOs and CFOs. You can no longer satisfy an auditor with a generic firewall and a policy binder tucked in a drawer. The "paper compliance" era is dead.
Regulators have stopped asking if you have a plan. They are now demanding proof that it works.
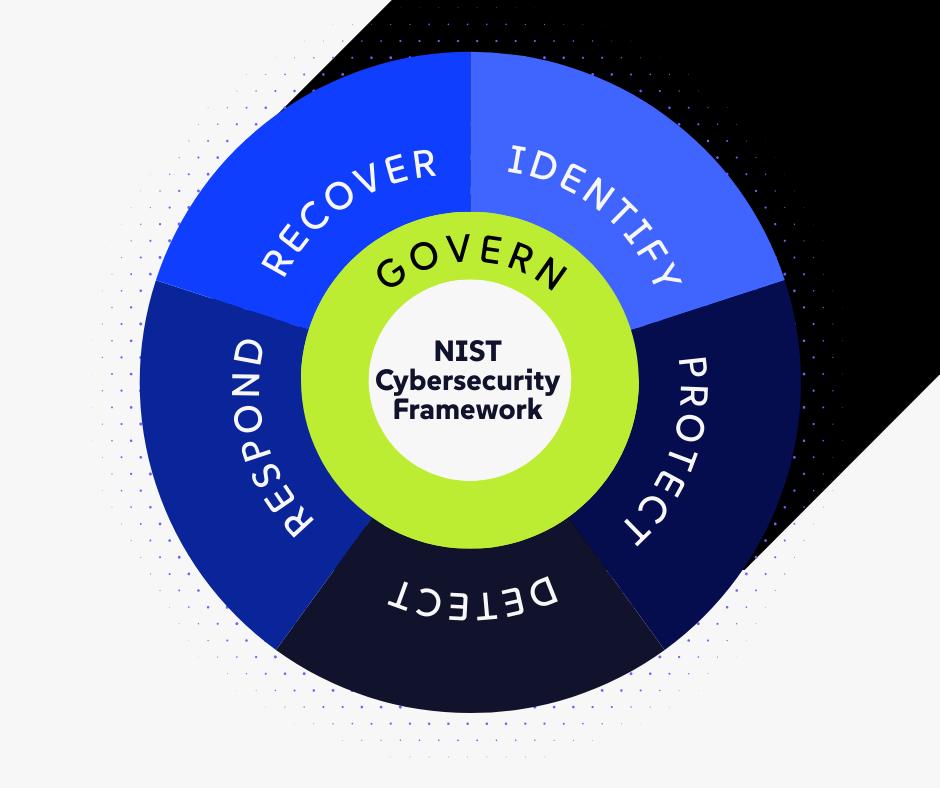
This ambiguity is the trap. The regulations rarely tell you exactly which software to buy, yet they hold you liable if your choices fail. To survive this scrutiny, you need a defense that is defensible. You need the NIST Cybersecurity Framework (CSF).
While not explicitly mandated by every regulation, NIST is the unofficial "gold standard" the industry uses to grade your homework. Aligning with NIST is the surest way to demonstrate that you are meeting the high expectations of the SEC, FINRA, and NYDFS.
If you are unsure whether your company needs to implement the framework, take our short assessment and read on for a deep dive into how NIST helps financial orgs ace their compliance audits and improve their cybersecurity efforts.
The High Stakes of Financial Cybersecurity
Reality Check: The Cost of Non-Compliance (2024-2025)
Your Blueprint for "Reasonable" Security
A Scenario: The "CEO Fraud" Test
The Third-Party Risk Factor (Supply Chain)
The November 1, 2025, Deadline (NYDFS)
Key Takeaway: Reasonable Security is a Moving Target
Frequently Asked Questions About NIST CSF for Financial Services
The High Stakes of Financial Cybersecurity
The financial sector is a primary target for cybercriminals for a distinct reason: you hold the money, and you trade on trust.
The costs of failure are astronomical. According to the 2024 IBM Cost of a Data Breach Report, the financial services industry has the second-highest breach costs of any sector (trailing only healthcare). The average cost of a data breach in financial services is now $6.08 million.
But for wealth managers, hedge funds, and broker-dealers, the $6 million price tag is only the beginning. The true cost lies in the regulatory fallout and the reputational extinction event.
- SEC Fines: The SEC has ramped up enforcement actions against firms that fail to safeguard customer records (Regulation S-P) or manage cybersecurity risks, with fines regularly reaching seven figures.
- NYDFS 23 NYCRR 500: This is one of the strictest cybersecurity regulations in the nation. It requires C-level certification of compliance. If you certify compliance and are later found to be negligent, you face personal liability.
Calculate the cost of a breach for your business with our cybersecurity calculator.
Reality Check: The Cost of Non-Compliance (2024-2025)
Regulators are no longer issuing warnings; they are issuing fines. Recent enforcement actions signal a zero-tolerance policy for "paper compliance."
- SEC vs. Flagstar Financial (Dec 2024): The bank paid $3.5 million for failing to disclose the full scope of a cyber breach. The lesson? Minimizing the truth is now considered securities fraud.
- SEC vs. Unisys & Avaya (Oct 2024): Four companies were charged a combined $7 million for misleading disclosures. The SEC explicitly stated that describing a risk as "hypothetical" when it has already happened is a violation.
- FINRA vs. Osaic Wealth (2024): Fined $150,000 per firm for failing to implement Multi-Factor Authentication (MFA) across all branch offices. This confirms that basic controls are now non-negotiable.
Your Blueprint for "Reasonable" Security
The NIST Cybersecurity Framework acts as a translator. It takes the dense, legalistic language of regulations and translates it into a clear, actionable roadmap for your IT and compliance teams.
Here is how the NIST functions map to your regulatory obligations:
1. Govern: The Boardroom Responsibility
The SEC’s recent rules emphasize that cybersecurity is a governance issue, not just a tech issue. The Govern function requires that leadership understands and manages cyber risk just as they manage market risk.
- The Regulatory Expectation: FINRA Rule 3110 requires a supervisory system reasonably designed to achieve compliance.
- The NIST Solution: Establish a clear organizational structure where cyber risk is reported to the Board or Investment Committee. Budgeting must be aligned with risk tolerance. A "set it and forget it" IT budget is no longer acceptable.
2. Identify: You Can’t Protect What You Don’t Know
Financial firms are plagued by complexity: trading platforms, custodian portals, shadow IT, and remote Bloomberg terminals. That's where the NIST Identify feature comes in.
- The Regulatory Expectation: The SEC requires you to oversee the risks associated with service providers and vendors.
- The NIST Solution: The Identify function mandates a comprehensive asset inventory. You must identify every location where Non-Public Personal Information (NPI) lives. This includes third-party vendors (TPRM). If your custodian gets breached, how does that impact your firm? NIST forces you to map these dependencies.
3. Protect: The Wire Fraud Shield
Wire fraud is the nightmare scenario for every CFO. The Protect function focuses on safeguards to ensure delivery of services and data security.
- The Regulatory Expectation: NYDFS 23 NYCRR 500.12 strictly mandates Multi-Factor Authentication (MFA) for any individual accessing internal networks.
- The NIST Solution: Zero Trust Architecture. It demands "least privilege" access. A junior analyst should not have the permissions to authorize a wire transfer or access the master client list. NIST pushes for technical enforcement (like impossible travel alerts and conditional access) rather than relying on policy alone.
4. Detect: Finding the Needle in the Haystack
Attackers are increasingly using "living off the land" techniques—using legitimate credentials to move quietly through a network.
- The Regulatory Expectation: The SEC’s proposal on Cybersecurity Risk Management requires advisors to have policies reasonably designed to detect cybersecurity incidents.
- The NIST Solution: The Detect function moves you from passive antivirus to active 24/7 monitoring (Managed Detection and Response - MDR). In finance, this means correlating user behavior. If a wealth advisor suddenly downloads 500 client PDF files at 2:00 AM, your system must detect that anomaly immediately.
5. Respond: The 4-Day Disclosure Clock
The SEC adopted new rules requiring public companies to disclose material cybersecurity incidents within four business days of determining materiality. While this strictly applies to public registrants, the standard is trickling down to RIAs and private funds as a best practice for "timely notification."
- The NIST Solution: The Respond function forces you to have a tested Incident Response Plan (IRP). When a breach happens, you do not have time to Google "what to do." You need a pre-planned playbook that involves Legal, Compliance, and PR.
6. Recover: Market Resilience
In finance, "downtime" equals "market risk." If you cannot trade during a volatile market session because your systems are locked by ransomware, the liability is immense.
- The Regulatory Expectation: FINRA Rule 4370 requires member firms to create and maintain a Business Continuity Plan (BCP).
- The NIST Solution: The Recover function distinguishes between restoring a server and restoring the business. It demands that you have a plan to communicate with clients and execute trades manually or via alternative systems if your primary infrastructure fails.
A Scenario: The "CEO Fraud" Test
To understand the value of NIST, look at a common attack vector: Business Email Compromise (BEC).
The Scenario: A hacker compromises the CFO’s email account. They watch conversations for weeks. Finally, they send an urgent email to the Controller: "I'm in a meeting. Wire $450,000 to this vendor immediately for the acquisition. It must clear today."
The "Compliance-Only" Firm:
They have a firewall. They have a policy against wire fraud. But they lack active detection. The Controller sees the email from the real CFO's account. They process the wire. The money is gone.
- Result: $450k loss, potential client lawsuits, and an SEC investigation into "failure to supervise."
The NIST-Aligned Firm:
- Protect: The CFO’s email requires MFA, making the initial compromise harder.
- Detect: The system flags an "impossible travel" login (the CFO logged in from New York, but the hacker logged in from Lagos 10 minutes later).
- Govern: The firm has a strict verification policy (governance) that requires voice confirmation for all wires over $50k.
- Result: The Controller receives the email but calls the CFO on their cell. The fraud is exposed. Zero loss.
The Third-Party Risk Factor (Supply Chain)
Financial services firms are increasingly reliant on third-party vendors, from cloud providers (AWS/Azure) to fintech applications and custodians.
Regulators are laser-focused on this. The NYDFS has specific requirements for "Third-Party Service Provider Security Policy."
NIST CSF provides the framework for this through its Supply Chain Risk Management (SCRM) category. It requires you to:
- Identify critical vendors.
- Assess their security posture (do they have a SOC 2 report?).
- Monitor their performance.
Visualize Your Vendor Risk: Imagine a "Red, Yellow, Green" scorecard for your top vendors.
- Green: They have a SOC 2 Type II report, robust MFA, and a clean penetration test.
- Yellow: They provide a self-assessment questionnaire, but lack independent third-party audit reports.
- Red: They have no dedicated security leadership, a history of past incidents, or use unencrypted public cloud storage for your data.
- Action: If your Custodian or CRM falls into the "Red" category, you are compliant... until they are breached. Then, you are negligent.
Data Point: The Verizon Data Breach Investigations Report (DBIR) indicates that the financial sector is disproportionately affected by credentials-based attacks and supply chain compromises.

The November 1, 2025 Deadline (NYDFS)
If you are subject to NYDFS 23 NYCRR 500, the clock is ticking. By November 1, 2025, covered entities must meet strict new requirements for:
- Asset Inventory: You must have a complete, written inventory of every information system, tracked by owner, location, and support expiration.
- Universal MFA: Multi-Factor Authentication is no longer just for remote access; it is required for all access to information systems, internally and externally.
Key Takeaway: Reasonable Security is a Moving Target
"Reasonable security" changes over time. What was reasonable in 2020 is negligence in 2025.
Adopting the NIST Cybersecurity Framework does not guarantee you will never be hacked. No framework can promise that. However, it does provide the most robust defense available, both against cybercriminals and against regulatory penalties.
When the regulators ask, "What did you do to prevent this?" you want to be able to show them a mature, NIST-aligned strategy. Anything less is a gamble with your firm's future.
Frequently Asked Questions About NIST CSF for Financial Services
-
Is the NIST Cybersecurity Framework mandatory for financial firms?
While not every regulation explicitly mandates "NIST" by name, it is widely considered the industry benchmark for "reasonable security." Regulators like the SEC, FINRA, and NYDFS use NIST standards to evaluate your defense. Adopting NIST is the most effective way to demonstrate due diligence and avoid negligence claims during an audit or post-breach investigation.
-
What does the SEC actually mean by "Reasonable Security"?
"Reasonable security" is a legal standard, not a technical one. It means your cybersecurity measures must match your specific risk profile and the complexity of your operations. It requires proof that your controls (such as MFA, encryption, and continuous monitoring) are implemented, tested, and actively working—policy binders alone are no longer sufficient.
-
Can a CFO or CCO be held personally liable for a cyber breach?
Yes, increasingly so. Under regulations like NYDFS 23 NYCRR 500, senior officers must certify compliance annually. If you certify compliance while knowing of significant gaps, you can face personal liability. Additionally, the SEC views cybersecurity oversight as a core fiduciary duty; failure to oversee risk can lead to "failure to supervise" charges.
-
What are the new NYDFS requirements coming in November 2025?
By November 1, 2025, covered entities under NYDFS must maintain a complete, written asset inventory that tracks every system's owner, location, and support expiration. Furthermore, strict Multi-Factor Authentication (MFA) will be required for all access to information systems (internal and external), removing previous exceptions for local access.
-
If our third-party vendor gets breached, is our firm liable?
Yes. Under Regulation S-P and general fiduciary standards, you cannot outsource your regulatory liability. You are responsible for safeguarding client data regardless of where it resides. You must perform Supply Chain Risk Management (SCRM)—a core NIST component—to assess and monitor the security posture of your vendors and custodians.
-
How does the NIST framework help prevent wire fraud?
NIST prevents wire fraud by layering defenses across its functions. Protect ensures MFA is on email accounts to prevent takeover. Detect spots anomalous login behavior (like impossible travel). Govern mandates strict policies, such as requiring voice verification for transactions over a certain dollar amount. Technology alone cannot stop fraud; governance is required.
-
Does a small RIA or hedge fund really need a full NIST program?
Yes. Attackers frequently target smaller firms because they are perceived as "soft targets" with high-value assets. Furthermore, regulations like Regulation S-P apply regardless of AUM. While a small firm’s implementation will be less complex than a major bank’s, the requirement to Identify, Protect, and Detect remains the same.
-
What is the SEC's "4-Day Rule" regarding cyber incidents?
The SEC now requires public companies to disclose material cybersecurity incidents via Form 8-K within four business days of determining materiality. While this strictly applies to public registrants, private funds and broker-dealers should view prompt notification to clients and regulators as a mandatory standard of care to avoid accusations of fraud or misleading omissions.
-
How does NIST differ from a standard IT audit?
An IT audit is a snapshot in time—a "pass/fail" check of specific controls. The NIST Cybersecurity Framework is a continuous, risk-based program. It focuses on the lifecycle of a threat (from prevention to recovery) and integrates cybersecurity into your business strategy, whereas an audit simply checks if a specific tool is installed.
-
How much does it cost to implement the NIST Cybersecurity Framework?
The cost varies by complexity, but the more important metric is the cost of non-compliance. With the average financial sector breach costing $6.08 million and fines reaching seven figures, the investment in a vCISO-led NIST program is a fraction of the potential loss. A vCISO can prioritize high-impact controls first to maximize ROI.