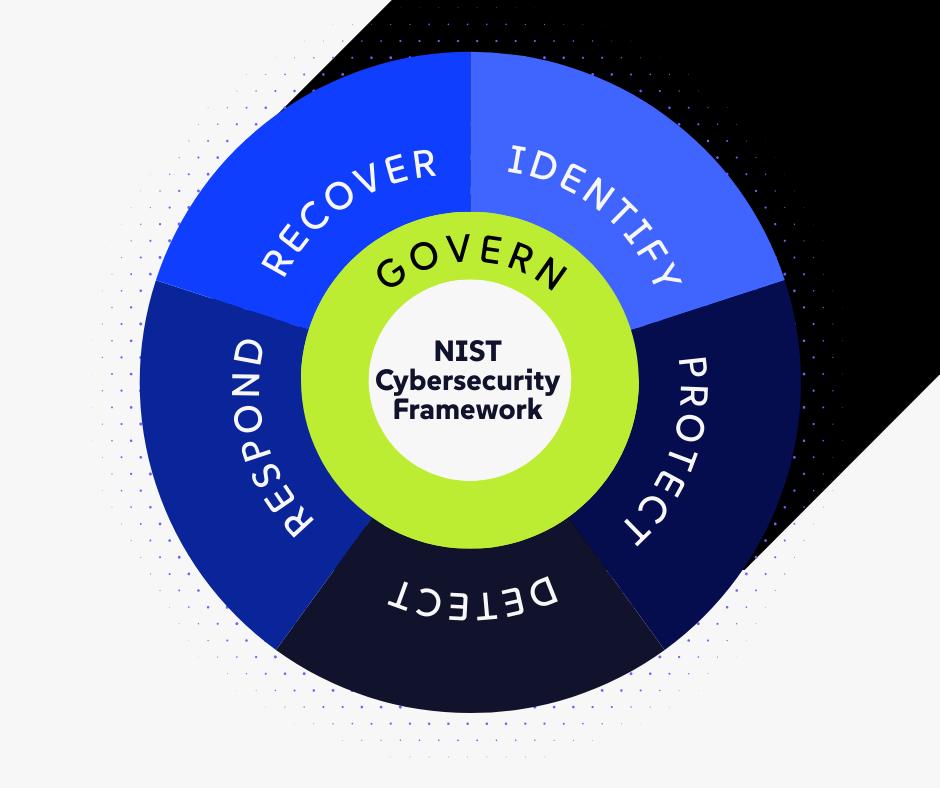
For a decade, the NIST Cybersecurity Framework (CSF) has been the "gold standard" for managing cyber risk. It was built on five famous pillars: Identify, Protect, Detect, Respond, and Recover.
If you walked into a board meeting in 2023, those five words were the entire conversation.
But in 2024, NIST released CSF 2.0, the most significant update in the framework’s history. They didn’t just tweak the language; they added a sixth, foundational function that sits above all the others: GOVERN.
As your vCISO, I can tell you this was a signal to the business world.
The addition of the "Govern" function explicitly states that cybersecurity is no longer a technical problem to be solved by your IT department. It is an enterprise risk that must be owned, funded, and overseen by senior leadership and drives accountability into the C-Suite.
This guide will walk you through the differences between version 1.1 and 2.0, why the "Govern" function was added, and how you can use it to build a defensible, top-down security strategy.
Executive Cheat Sheet: NIST 1.1 vs. 2.0
The Core Shift: From "IT Operations" to "Enterprise Risk"
The 6 Pillars of the New "Govern" Function
Self-Assessment: What is Your Governance Maturity?
Why This Change Matters for the C-Suite (The "Why Now?")
How a vCISO Helps You Upgrade from 1.1 to 2.0
3 Hard Questions for Your Next Board Meeting
Your Next Step: Don't Wait for the Alarm
Frequently Asked Questions About NIST CSF 2.0 and the Govern Function
Executive Cheat Sheet: NIST 1.1 vs. 2.0
If you only have two minutes, look at this table. It summarizes the fundamental shift in how your organization is expected to manage security.
|
Feature |
NIST 1.1 (The Old Way) |
NIST 2.0 (The New Way) |
The Business Implication |
|
The Structure |
5 Functions (Identify, Protect, Detect, Respond, Recover). |
6 Functions (Added GOVERN). |
Cybersecurity is now a Board/C-Suite responsibility, not just an IT task. |
|
The Focus |
Critical Infrastructure (Power, Water, Finance). |
All Organizations (Any sector, any size). |
"We're too small/not critical" is no longer a valid excuse. |
|
Supply Chain |
A minor sub-category. |
A Major Pillar (GV.SC). |
You are now directly accountable for the security of your vendors. |
|
Governance |
Buried inside "Identify." |
The Centerpiece. |
Strategy drives technology. You must define "risk appetite" before buying tools. |
|
The Goal |
"How do we secure our systems?" |
"How do we manage Enterprise Risk?" |
Security must align with your business mission and budget. |
The Core Shift: From "IT Operations" to "Enterprise Risk"
To understand the change, you have to look at the structure.
- In NIST CSF 1.1 (The Old Way): Governance was a small sub-category tucked away inside the "Identify" function. It was treated as a paperwork exercise—"Do we have a policy? Check."
- In NIST CSF 2.0 (The New Way): "Govern" is now a standalone function. In the official diagram, "Govern" is placed in the center of the wheel, touching and influencing all other functions (Identify, Protect, Detect, Respond, Recover).
THE MESSAGE:
You cannot "Protect" or "Detect" effectively if you do not first "Govern."
Without governance, your security program is just a collection of expensive tools with no strategy. The "Govern" function mandates that your cybersecurity strategy must align with your business mission, your risk tolerance, and your budget. From a culture perspective, every role in an organization is a “Risk Manager” and needs to incorporate that mindset into the day-to-day operations.
The 6 Pillars of the New "Govern" Function
The "Govern" function is broken down into six categories. As a vCISO, I translate these from "NIST-speak" into executive action items:
1. Organizational Context (GV.OC)
The Question: "Does our security strategy match our business reality?" The Shift: You can't copy-paste a bank's security policy into a manufacturing plant. This category requires you to define your specific mission, stakeholders, and legal requirements.
- Example: If you are a DoD contractor, your "Organizational Context" includes CMMC compliance. If you are a law firm, it includes client privilege.
2. Risk Management Strategy (GV.RM)
The Question: "What is our risk appetite?" The Shift: This is the most critical conversation a vCISO has with a CEO. We must define what risks you are willing to accept, avoid, or transfer (insurance). Also, are you reviewing and adjusting your risk profile dynamically? Nothing is stagnet, so if your business moves in a new direction, then your risk landscape changes and processes and messaging may need to shift as well.
Data Point: This is crucial when 45% of organizations are expected to experience a software supply chain attack by 2025, according to Gartner. You must decide: do we accept the risk of using that cheap software vendor, or do we pay more for a secure one?
3. Roles, Responsibilities, and Authorities (GV.RR)
The Question: "Who goes to jail if this goes wrong?" The Shift: This moves beyond "IT handles security." It requires assigning specific security responsibilities to the CEO, the Board, HR, and Legal. It establishes accountability.
The Question: "Who goes to jail if this goes wrong?" The Shift: This moves beyond "IT handles security." It requires assigning specific security responsibilities to the CEO, the Board, HR, and Legal. It establishes accountability.
4. Policy (GV.PO)
The Question: "Are our rules written down and approved?" The Shift: Policies must be living documents, approved by leadership, and communicated to staff. A policy is just words on paper without procedure to implement the controls and a defined approach to evidence and show that the steps are operating effectively.
5. Oversight (GV.OV)
The Question: "How do we know it's working?" The Shift: This mandates a standardized way to measure performance. It moves you from "I think we're secure" to "Here is our monthly metric report showing a 20% reduction in phishing clicks."
6. Cybersecurity Supply Chain Risk Management (GV.SC)
The Question: "Do we trust our vendors?" The Shift: In version 1.1, supply chain was an afterthought. In 2.0, it is a headline. You are now responsible for the security of your vendors. If your payroll processor gets hacked, NIST 2.0 says you are responsible for governing that risk.
Self-Assessment: What is Your Governance Maturity?
Where does your organization stand today? Read these three profiles. Be honest.
|
Maturity Level |
Executive Mindset |
Strategy & Budget |
Board Reporting |
NIST Status |
|
RED (Low Maturity) |
"Cybersecurity is the IT department's problem." |
No formal budget. Tools are bought reactively after a scare. |
The Board only hears about security when something breaks or requires a crisis response. |
Non-compliant with the "Govern" function. |
|
YELLOW (Medium Maturity) |
"We need to pass the audit." |
Policies exist but are rarely updated. Cyber insurance is in place, but the Incident Response (IR) plan is untested. |
Annual updates to the Board, often focused solely on technical jargon and compliance checkboxes. |
Elements of "Govern" are present, but they are disconnected from core business strategy. |
|
GREEN (High Maturity) |
"Cyber risk is business risk." |
Security is a standing item on the Board agenda. Budgets are risk-based and proactive. |
Quarterly reviews with a vCISO focused on quantifiable risk reduction, ROI, and business continuity. |
Fully aligned with NIST CSF 2.0. |
Why This Change Matters for the C-Suite (The "Why Now?")
NIST didn't make these changes for fun. They made them because the threat landscape—and the regulatory landscape—this is a paradigm shift..
1. The SEC & Regulatory Pressure
The SEC's new rules for public companies (and the trickle-down effect to private firms) demand "material" incident disclosure and board-level oversight. The "Govern" function is essentially the blueprint for meeting these SEC requirements. If you follow NIST 2.0, you are naturally building the governance structure regulators demand.
2. The Failure of "Bottom-Up" Security
For years, IT directors tried to push security "up" to the board. It failed. Budgets were cut, and risks were ignored. NIST 2.0 flips the model. It mandates "Top-Down" security. The strategy is set by the board ("Govern") and executed by IT ("Protect").
3. The Cost of Chaos
Without governance, incident response is chaos. The IBM 2024 Cost of a Data Breach Report highlights that organizations with high levels of security system complexity (a symptom of poor governance) faced an average breach cost of $3.84 million, significantly higher than those with simplified, governed architectures. Governance simplifies complexity.
How a vCISO Helps You Upgrade from 1.1 to 2.0
Moving from NIST 1.1 to 2.0 isn't about buying new software. It's about upgrading your management operating system.
Most SMBs do not have the internal expertise to build a "Risk Management Strategy" or a "Supply Chain Oversight Program." This is exactly where a vCISO provides value.
The CompassMSP Approach to "Govern":
- Gap Analysis: We don't guess. We measure your current program against the 6 "Govern" categories.
- Policy Development: We author the executive-level policies (Acceptable Use, Incident Response, Vendor Risk) that 2.0 demands.
- Board Reporting: We act as the translator, presenting quarterly "Oversight" (GV.OV) reports to your leadership in plain English, not tech-speak.
- Supply Chain Review: We implement a Vendor Risk Management program to satisfy the new GV.SC requirements.
NIST CSF 2.0 is an opportunity. It’s a chance to stop treating cybersecurity as a terrifying IT cost center and start treating it as a governed, managed business function
3 Hard Questions for Your Next Board Meeting
Empower your leadership team by asking these three questions. The answers will tell you if you are truly governing risk.
- "Does our current security strategy align with our business goals, or is it just driven by the IT budget?" (If the answer is 'IT budget,' you are in the Red zone).
- "Who is the specific executive named in our policy as accountable for cyber risk?" (If the answer is 'the IT guy,' you fail the GV.RR requirement).
- "Who is the specific executive named in our policy as accountable for cyber risk?" (If the answer is 'the IT guy,' you fail the GV.RR requirement).
- "Do we have a list of our critical vendors, and have we audited their security this year?" (If not, you are exposed to supply chain risk).
Your Next Step: Don't Wait for the Alarm
You now know the financial stakes. The difference between a $2.9 million breach and a $4.39 million breach is a tested plan.
Do not wait for a crisis to meet your Incident Commander.
Is your organization ready for the 2:00 AM test? CompassMSP offers a complimentary vCISO Strategy Session for qualified organizations. In this 30-minute consultation, we will:
- Review your current Incident Response maturity.
- Identify the biggest "Respond" gaps in your governance.
- Show you how a vCISO-led program can build your resilience in 90 days.
Prefer to start with the numbers? Use our Cybersecurity ROI Calculator to see exactly what a breach could cost your specific business, and how much an IRP could save you.
Frequently Asked Questions About NIST CSF 2.0 and the Govern Feature
-
Is NIST CSF 2.0 mandatory?
For most private businesses, it is voluntary. However, it is the standard of care used by courts, insurance carriers, and regulators (like the FTC and SEC) to define "reasonable security." Ignoring it is a liability risk.
-
We are a small business. Is "Governance" too complex for us?
No. Governance scales. For a small business, "Governance" might just mean a quarterly meeting between the CEO and the MSP to review risks and approve a budget. NIST 2.0 is designed to be "size-agnostic."
-
What happens to our existing NIST 1.1 assessment?
It is not wasted. The core functions (Identify, Protect, Detect, Respond, Recover) are largely the same. You simply need to "layer on" the new Govern function. A vCISO can map your old 1.1 assessment to the new 2.0 standard.
-
Does "Supply Chain Risk Management" mean I have to audit Microsoft?
No. It means you need a process to evaluate your vendors based on their criticality. You don't audit Microsoft, but you do verify that your local payroll provider has a SOC 2 report. That is "Reasonable" governance.
-
Can I implement NIST 2.0 without a CISO?
Technically, yes. Practically, no. The "Govern" function requires specialized knowledge of risk management frameworks, policy writing, and compliance. If you can't afford a full-time CISO, a vCISO is the purpose-built solution to fulfill this specific NIST requirement.
-
Lorem ipsum dolor sit amet consectetur adipisicing elit?
Lorem ipsum dolor sit amet consectetur adipisicing elit. Maxime mollitia, molestiae quas vel sint commodi repudiandae consequuntur voluptatum laborum numquam blanditiis harum quisquam eius sed odit fugiat iusto fuga praesentium optio, eaque rerum! Provident similique accusantium nemo autem. Veritatis obcaecati tenetur iure