Every budget season, the same conversation resurfaces. Everyone agrees cybersecurity is important, but when it’s time to assign real dollars, the discussion drifts into uncertainty.
For small and mid-sized businesses, this tension is especially real. You’re trying to make smart tradeoffs with limited dollars, unclear benchmarks, and cybersecurity trends that change faster than your forecast.
This guide reframes cybersecurity budget planning in the language that CFOs and COOs speak. It replaces fear-based spending with a practical planning framework, one that turns cybersecurity from a vague, reactive expense into a predictable, strategic investment you can explain and defend.
Why Cybersecurity Has to Be a Line Item, Not a Leap of Faith
The Financial Imperative: Cybersecurity Cost vs. Risk
A Cybersecurity Budgeting Framework for CFOs and COOs
The Role of a vCISO in Cybersecurity Budget Planning
FAQ: A vCISO Answers Top Cybersecurity Budgeting Questions
Why Cybersecurity Has to Be a Line Item, Not a Leap of Faith
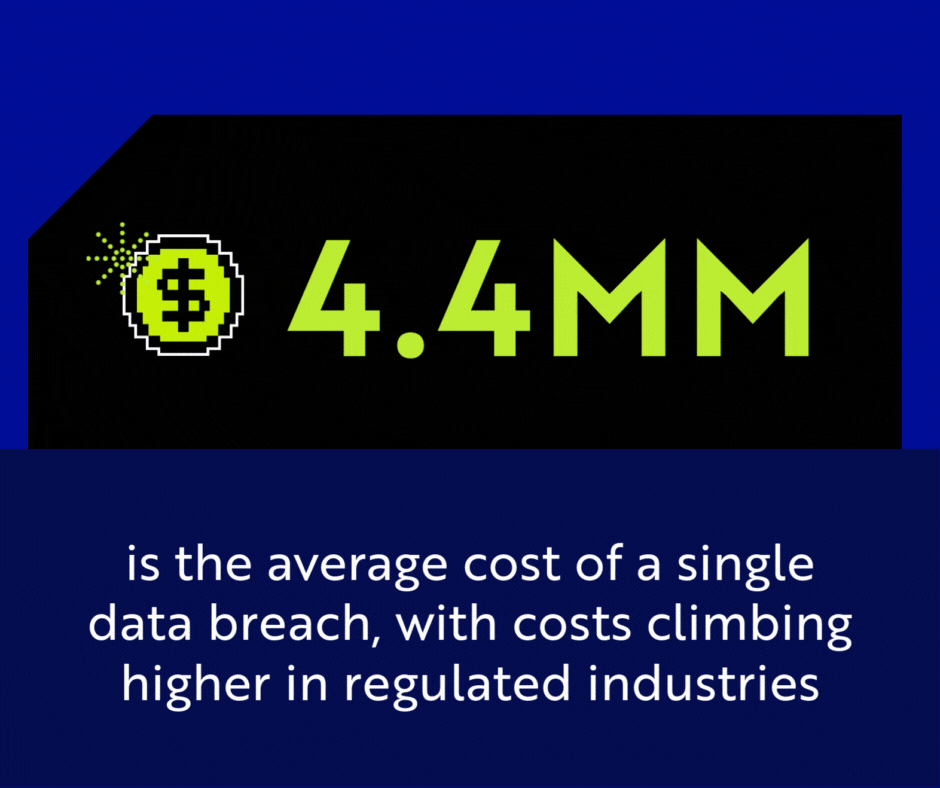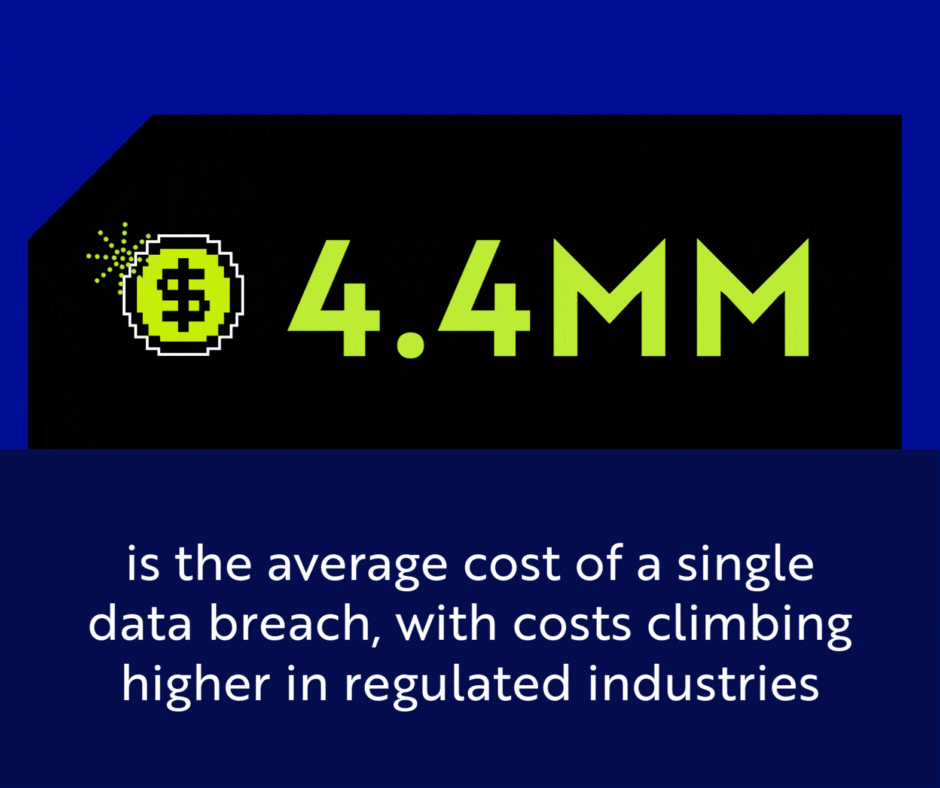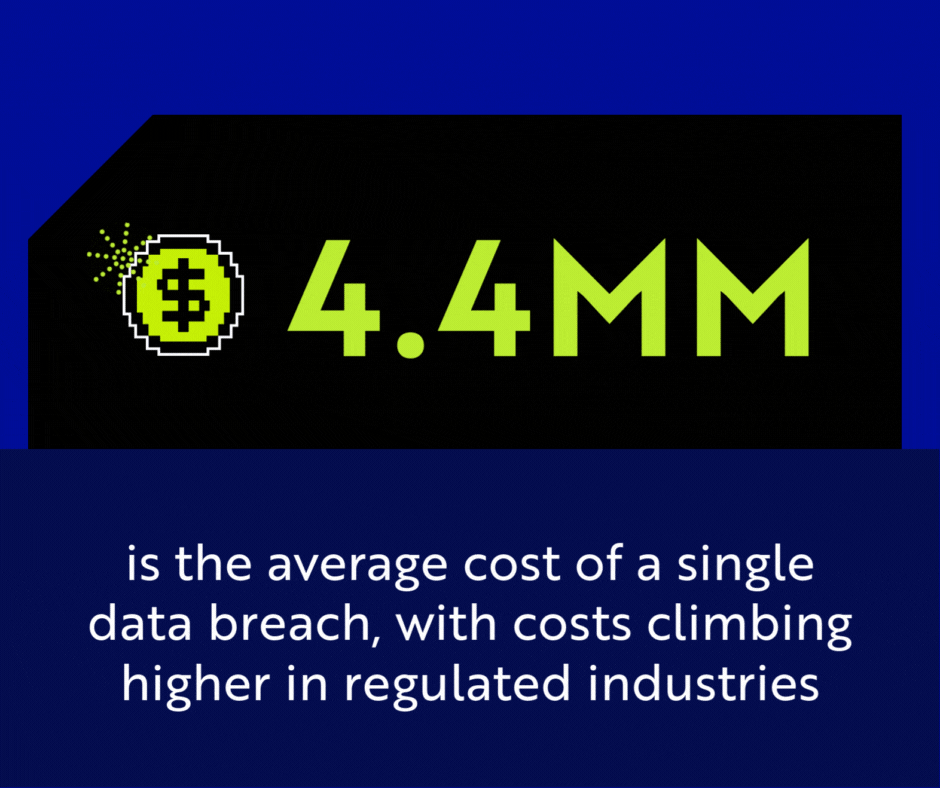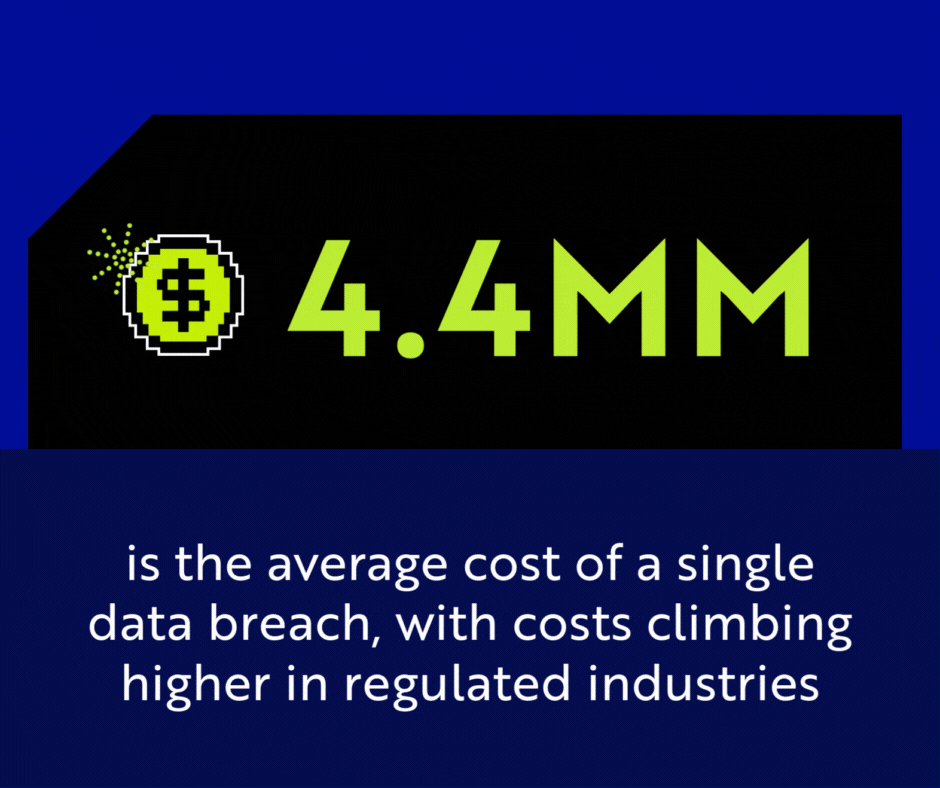
Let’s ground this in numbers before we talk frameworks. IBM’s Cost of a Data Breach Report reported the global average cost of a breach was $4.4 million.
Meanwhile, PwC’s most recent Digital Trust Insights revealed that nearly 80% of organizations now expect their cybersecurity budgets to grow, with data protection sitting at the top of the investment priority list.
These numbers tell a consistent story: cybersecurity has shifted from an IT concern to a critical business risk category, right alongside financial controls, legal exposure, and supply chain resilience.
Despite the numbers, many small businesses still struggle to treat cyber risk as business risk. Your job isn’t to throw money at security. Your job is to decide how much risk your business can responsibly carry and fund a program that matches that reality.
The Financial Imperative: Cybersecurity Cost vs. Risk
For CFOs and COOs, the most important shift to make is reframing what cybersecurity cost vs. risk looks like. An upfront investment in strategic security isn’t just an IT expense; it’s an insurance policy against the cost of a data breach. For growing businesses, that impact can be existential.
The financial fallout doesn’t stop with IT cleanup:
- Financial impact: Research shows the average cost of a data breach for businesses with fewer than 500 employees is $3.31 million. That’s not pocket change. Even when small business breaches typically cost less in absolute dollars, they consume a much larger share of revenue and operating capacity, making recovery far more difficult.
- Downtime impact: As any COO knows, forced downtime is brutal for business continuity. Research found that over 40% of small to mid-sized businesses with 200 employees estimated their cost of downtime to be $1 million per hour in lost productivity, missed revenue, and disrupted business operations.
And that’s just scratching the surface. Add in regulatory fines, higher cyber insurance premiums, customer churn, and long-term reputational damage. In the worst cases, companies never recover.
In fact, one study found that one in five small businesses either shut down or filed for bankruptcy after a cyberattack. Suddenly, a small business cybersecurity budget looks like the most critical investment you can make in maintaining revenue stability.
Below is a practical cybersecurity budgeting framework you can use in your next planning cycle. It shifts the conversation from tools to business outcomes, from fear to smart tradeoffs, and from a one-year scramble to a three-year security roadmap.
A Cybersecurity Budgeting Framework for CFOs and COOs
This roadmap gives boards and business owners confidence that a cybersecurity investment is strategic rather than reactive. It also allows CFOs and COOs to spread capital impact across multiple years instead of absorbing it all at once.
Step 1: Define What You’re Protecting
Cybersecurity budgets get complicated when teams define protected assets too broadly. “The network,” “the data,” or “the systems” are too abstract. CFOs and COOs operate best with specificity.
In practical terms, most small businesses are protecting three core categories:
- Revenue-generating systems: Platforms that directly support billing, production, customer transactions, or service delivery.
- Sensitive data: Customer records, payment data, PHI, IP, trade secrets, pricing models.
- Critical operations: Systems that, if unavailable for even a few days, would disrupt contracts, payroll, logistics, or regulatory obligations.
Once you clearly define these assets, cybersecurity strategy becomes easier to model financially. The cybersecurity budget discussion moves away from vague threat scenarios and toward concrete business exposure.
Step 2. Translate Cyber Risk into Financial Terms
Next, translate cyber risk into a format you’re fluent in: expected financial impact. For each asset or critical system, estimate:
1. Single-incident impact- Lost revenue (downtime, churn, missed SLAs)
- Recovery costs (forensics, legal, PR, overtime, vendors
- Fines and penalties (regulatory, contractual)
- Longer-term damage (churn, lost deals, higher insurance)
As a sanity check, remember that the average breach runs around $4–5 million, even before you get into heavy regulation or high-value IP. For a small business, you may land below that number, but it’s still meaningful.
Even a “small” cyber attack can cost you hundreds of thousands to low millions once you factor in business interruption.
2. Annual likelihoodThis doesn’t need to be perfect. Use ranges:
- Low: 1–5% chance per year
- Medium: 6–15%
- High: 16–30%+
Now, multiply the estimated impact by the estimated likelihood to get a rough estimate of expected annual loss:
Expected loss ≈ Single-incident impact × Likelihood
This is your starting point. It doesn’t have to be perfect; it simply creates a baseline that answers what level of cyber-related financial loss your business is willing to accept.
Step 3: Set a Risk Appetite the Business Can Defend
You can’t eliminate all risk, but you should be intentional with accepted risk. Risk appetite defines the level of potential cyber loss the company is prepared to absorb without destabilizing operations, triggering layoffs, breaching covenants, or derailing strategic growth.
For some organizations, that might be a few hundred thousand dollars per year. For others, it may be more. When expected cyber losses exceed that tolerance, investment becomes a necessity rather than a discretionary upgrade. The cybersecurity budget then represents the capital required to bring risk into a tolerable range over a realistic timeframe, which is typically two to three years.
Step 4: Use Simple Budget Guardrails Instead of Arbitrary Percentages
There is no universal “correct” cybersecurity budget percentage. However, industry data provides useful guardrails that small business leadership can follow:
- Utilize the 0.5% to 1.5% benchmark: Industry benchmarks suggest small businesses typically spend between 3.5% and 8% of annual revenue on total IT. A strong cybersecurity program usually requires 10% to 15% of that IT budget to go directly toward security and compliance. In practical terms, that means setting aside roughly 0.5% to 1.5% of annual revenue specifically for cybersecurity.
- Adjust for your risk and complexity: Businesses in highly regulated industries (e.g., healthcare, finance, legal) often need to budget toward the higher end of this range. Same story for businesses with more cloud apps, AI tools, and a bigger remote workforce.
- Check against expected loss: If you’re carrying millions in expected cyber loss and spending a fraction of that on protection, the math probably doesn’t hold.
These benchmarks should not dictate spend, but they help validate whether internal risk tolerance and actual investment are aligned.
Step 5. Structure the Cybersecurity Budget for Predictability
Now comes the translation of strategy into line items. Cybersecurity becomes financially manageable when you structure the budget with intention. Stable, resilient programs separate spending into three clear functional categories:
- Sustain Operations
This is your baseline and what you must fund to maintain day-to-day security:
- Existing security tools and platforms (endpoint, email security, firewalls, SIEM, backups)
- Managed security services, vCISO support, and monitoring
- Compliance maintenance and audits
- Basic employee training and phishing simulations
- Strengthen Existing Defenses
This is where you harden what you already have and close the most common gaps:
- Multifactor authentication everywhere it matters
- Identity and access management improvements
- Vulnerability management, patching, and system hardening
- Network segmentation and zero-trust fundamentals
- Backup modernization and recovery testing
- Vendor risk management and contract updates
- Prepare for Future Threats
This category prepares you for what’s next, not just what’s broken today:
- AI and automation for detection and response
- Security architecture upgrades (SASE, zero trust, cloud posture management)
- Data classification and DLP around your most important asset
- Major modernization projects, like retiring legacy systems that you can’t secure
This structure keeps your cybersecurity budget from turning into a reactive spending trap. It also gives CFOs real leverage to rebalance investments during economic pressure without weakening the critical protections the business depends on.
Step 6: Tie Every Dollar to Measurable Outcomes
One of the most consistent frustrations executives have with cybersecurity investment is the lack of business-level performance indicators. Tool dashboards rarely translate into board-ready outcomes.
To make cyber outcomes legible at the exec level, pick a small set of metrics that map to risk and resilience, such as:
- Time to detect and contain incidents. Research from IBM shows that faster detection and response reduce breach costs.
- Coverage of critical controls, such as multi-factor authentication (MFA) on critical systems, tested backups, and high-severity vulnerabilities remediated within 30 days
- Exposure reduction, like the number of internet-facing apps without MFA and high-risk vendors without security clauses
- Business-impact metrics, including security-related outages during business hours
and an estimate of avoided losses from blocked attacks
For each line item in your budget, add one simple sentence: “We’re funding this to move Metric X from A to B over Y months.”
That’s how you break the pattern of “We spent more, but we’re not sure what we got.”
Every major cybersecurity investment should be traceable to a measurable improvement in at least one of these areas. Once that link is clear, budget accountability becomes straightforward.
Step 7: Build a Multi-Year Cybersecurity Roadmap Instead of One-Year Fire Drills
Cybersecurity programs rarely succeed when planned for one budget cycle at a time. A multi-year cybersecurity roadmap provides financial predictability and operational sequencing that reduces wasted spend.
Most small businesses benefit from a steady progression rather than an aggressive single-year overhaul. A simple 3-year view might look like this:
Year 1: Stabilize and Close the Obvious Gaps
- Implement MFA everywhere critical
- Fix backup and recovery (test it, don’t just trust it)
- Harden and patch high-value systems
- Address a short list of “red flag” vendors
- Stand up basic monitoring and incident response playbooks
Year 2: Standardize and Automate
- Roll out better identity and access management
- Move to more unified security tooling where it makes sense
- Automate recurring security tasks (patching, log review, alerts)
- Tighten vendor risk management and contracts
- Formalize cybersecurity training for all staff
Year 3: Optimize and Align with Growth
- Revisit architecture (zero trust, SASE, cloud posture management)
- Use more advanced analytics and AI where appropriate
- Align cyber program with strategic moves (new markets, M&A, product launches)
- Adjust budgets based on real data from incidents and metrics
The Role of a vCISO in Cybersecurity Budget Planning
You don’t need a full-time CISO to achieve maturity. To fill security gaps, many small businesses:
- Lean on a vCISO for strategy guidance, governance, and board-level communication.
- Use a managed security provider for 24/7 monitoring and incident response.
- Keep a small in-house IT or security team focused on operations and coordination.
When you bring a vCISO or strategic partner into the discussion, make sure they speak in terms of risk reduction per dollar spent and business outcomes, not just improving your security posture.
Your Cybersecurity Investment Strategy Belongs in the Boardroom
Cybersecurity no longer lives on the margins of enterprise risk. It directly shapes revenue stability, regulatory exposure, insurance viability, and customer trust.
You don’t need to become a security expert to govern this category well. CompassMSP helps CFOs and COOs turn cybersecurity into a predictable, board-ready investment strategy. From vCISO-led planning to 24/7 security operations, we align protection to your financial and operational goals.
Reach out to our team if you are ready to make cybersecurity a strategic business asset instead of a budget wildcard.
FAQ: A vCISO Answers Top Cybersecurity Budgeting Questions
-
How much should a small or mid-sized business spend on cybersecurity?
While dependent on industry and regulation, a practical financial benchmark for a dedicated cybersecurity budget for a small business is generally 0.5% to 1.5% of annual revenue. This security allocation should typically account for 10% to 15% of the total IT spending.
-
What is cybersecurity ROI for small business, and how is it calculated?
Cybersecurity ROI for small businesses is really about losses avoided. You estimate the financial impact of a worst-case breach, then compare that risk to what you actually spend on protection. The “return” is simply the gap between what you could have lost and what you invested to prevent it.
-
How does a vCISO help with cybersecurity budget planning for a CFO?
A vCISO (Virtual Chief Information Security Officer) serves as the executive advisor who translates technical requirements into actionable cyber risk financial planning. They collaborate with the CFO to quantify risk, strategically prioritize all investments based on their financial impact, and develop the multi-year cybersecurity roadmap.
-
What is the most important factor for reducing cybersecurity cost vs. risk?
The most critical factor is the shift to proactive, end-to-end managed services. When you move away from the old “break/fix” model and into 24/7 monitoring and ongoing governance, you drastically reduce both the chance and the cost of major incidents. Just as important, you turn unpredictable emergency spending into a steady, predictable investment in downtime prevention.
-
What is the COO’s primary role in executing the cybersecurity investment strategy?
The COO plays a critical role by keeping the focus on operational risk and day-to-day execution. They make sure cybersecurity strategy is part of daily operations by supporting the adoption of new tools, processes, and policies across teams. They ensure performance stays consistent and compliance doesn’t slip.







