Your Guide to Avoiding Audit Failures
Many organizations believe they’re compliant, but that sense of security is often deceptive, especially for small and mid-sized businesses. This mindset leads to skipping the most critical step in the entire compliance lifecycle: the compliance gap analysis. Most failures lurk in the space between policy and execution, and once a regulator demands proof or an incident occurs, those cracks widen fast.
Compliance Officers and Risk Managers must stay ahead of all the evolutions of different frameworks, whether it’s HIPAA, PCI DSS, SOC 2, CMMC, NYDFS, or another industry-specific mandate. You need confidence that when an auditor walks through the door or a cyber-insurance renewal hits your desk, the organization is standing on solid ground.
Skipping a formal gap analysis doesn’t save time or money. It simply hides the debt and creates a false sense of security. This article explores the hidden costs of ignoring compliance gaps and outlines how to turn compliance audit readiness from a source of stress into a strategic advantage.
How a Compliance Gap Analysis Protects You from False Confidence
The Three-Step Compliance Gap Analysis That Prevents a $3.31M Loss
The Role of a vCISO: Gap-Analysis Compliance Officer
How to Turn Your Anxiety into Audit Readiness
How a Compliance Gap Analysis Protects You from False Confidence
Organizations often skip deep-dive assessments because of assumptions. IT teams assume their firewalls are configured correctly. Executives assume that having a policy document means the organization follows the policy.
A compliance gap analysis is the only mechanism that challenges these assumptions. It measures the distance between your current state (what is actually happening) and your desired state (what the framework requires). Without it, you are operating on hope.
The Visibility Void
When you skip a compliance gap analysis, you fly blind. For example, you think you have "access controls" in place, but a PCI DSS gap analysis reveals that three terminated employees still have active admin credentials. You believe your backups are sound, but a SOC 2 readiness assessment shows that the restore process hasn't been tested in 18 months. These are the compliance risk exposures that destroy audits.
When auditors arrive, they expect to see evidence, logs, configuration records, vendor due diligence files, you name it. If any of those are missing or incomplete, it often shows up as a material finding.
This can delay or block certification. Without certification or audit pass status, customer trust erodes, vendor relationships stall, and deals are lost. In highly regulated industries, that delay can mean millions in lost revenue or even contract cancellations.
Cost #1: The Financial Sting of Regulatory Fines and Penalties
Let's talk about the most direct consequence: money. Regulators are no longer lenient with organizations that claim ignorance. When compliance gaps remain unaddressed, you won’t get a slap on the wrist. You face penalties, fines, and, in some cases, operational restrictions.
In 2023, Wells Fargo faced $200 million in penalties for not adequately capturing and preserving electronic communications like calls and text messages. The SEC pointed to widespread breakdowns in oversight and documentation practices. These penalties reflect systemic failures in compliance, supervision, or security posture.
The Multiplier Effect of Negligence
If a breach occurs and the investigation reveals that the organization never conducted a proper assessment to find the vulnerability, the fines multiply.
- GDPR and NYDFS: These frameworks have aggressive penalty structures. Fines are often calculated not just based on the damage done, but on the lack of prevention. For example, GDPR violations can cost up to €20 million or 4% of annual revenue, whichever is higher.
- HIPAA: For healthcare organizations, HIPAA compliance gaps are expensive. For instance, an unencrypted laptop is a huge problem, a systemic failure to conduct a risk analysis (a specific HIPAA requirement) attracts the maximum penalty tiers.
Many organizations assume regulators penalize only after a breach, but in reality, enforcement often springs from audit failures, self-assessments, or vendor reviews. Failure to comply can cost far more than investing in a proper gap analysis.

Cost #2: The "Audit Shock" and Remediation Panic
There is a specific type of chaos that ensues when an external auditor finds a major non-conformity that should have been caught months ago. This is the cost of audit failure risks.
The root causes are typically predictable: poor documentation, using spreadsheets, inconsistent monitoring, and little to no vendor risk management. These are the same gaps that get exposed only in a real gap analysis.
In effect, failed audits are rarely “surprises.” They’re symptoms of a lack of rigor, process, and proof.
The Reactive Scramble
When an auditor flags a compliance gap, like a lack of multi-factor authentication (MFA), on a critical segment of the network, the organization enters crisis mode.
- Emergency Spending: To fix the gap instantly, you pay premium rates for emergency IT support, expedited software licensing, and after-hours labor.
- Operational Drag: Your internal teams drop all strategic projects to focus solely on remediation. The cost of this distraction is invisible on the balance sheet but massive in terms of lost productivity.
- Loss of Credibility: For a Compliance Officer, failing an audit undermines your authority with the C-Suite. It signals that the compliance risk management program is not under control.
A proactive compliance gap analysis prevents this fire drill. It allows you to identify the gap six months in advance and budget for the remediation calmly and strategically.
Cost #3: The Cyber Insurance Denial
The cyber insurance market has hardened significantly. Carriers no longer write policies based on simple questionnaires; they now demand proof of cyber insurance compliance.
The "Failure to Maintain" Clause
Insurance providers are increasingly using gap analysis logic to deny claims. If your policy application stated that you had "comprehensive patch management," but a post-breach forensic audit reveals significant regulatory compliance gaps in your patching cadence, the carrier may argue misrepresentation.
On top of this, insurers often require specific controls (like EDR, immutable backups, and MFA) as conditions for coverage. If you haven't performed a gap analysis against the insurer’s requirements, you may find your policy is void just when you need it most.
Beyond premiums, many insurers also require evidence of continuous compliance: access logs, patch records, vendor audits, incident-response readiness, and more. Without those, coverage can evaporate or cost more than implementing controls proactively.
Cost #4: Third-Party and Supply Chain Exclusion
For those targeting CMMC (Cybersecurity Maturity Model Certification) or working with enterprise clients, third-party risk compliance is the new gatekeeper.
Large enterprise clients now audit their vendors. If you are a supplier, you will receive security questionnaires that require evidence of compliance framework alignment. If you cannot demonstrate that you have identified and closed your gaps, you lose the contract.
For Defense Industrial Base (DIB) contractors, there is no "Plan of Action and Milestones" (POAM) allowed for certain critical controls. You either pass, or you cannot bid on the contract. For organizations required to comply with CMMC standards, a compliance gap assessment is the only way to ensure you don't lose revenue eligibility.
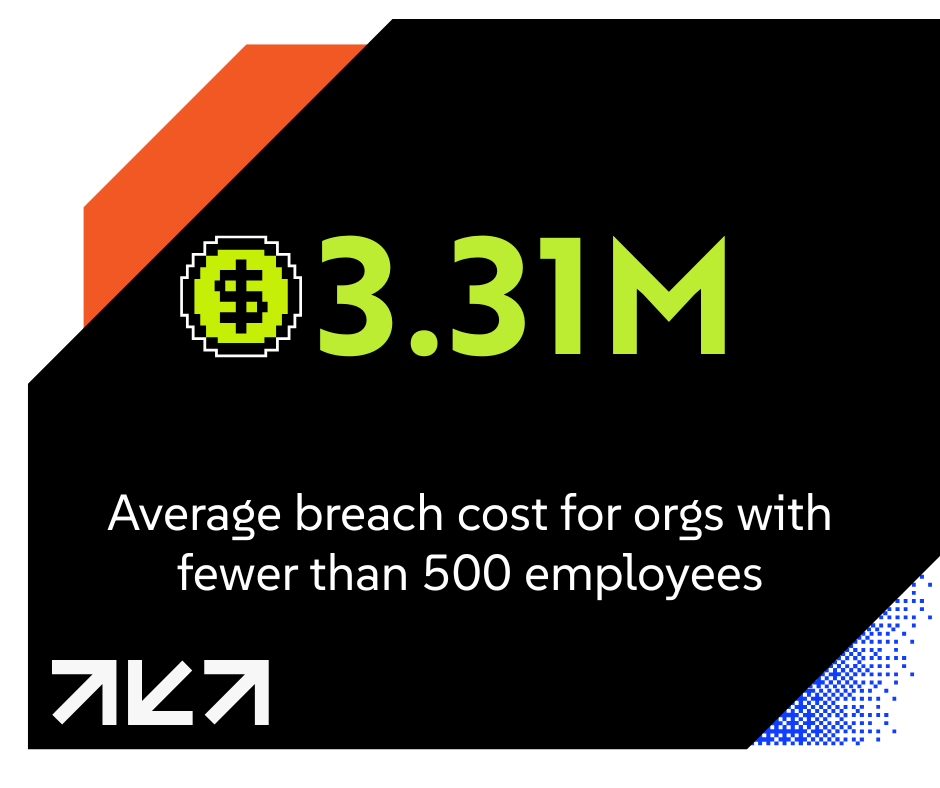
The Three-Step Compliance Gap Analysis That Prevents a $3.31M Loss
Given that the average cost of a data breach for businesses with fewer than 500 employees is $3.31 million, any preventable step counts. Here’s what a comprehensive gap analysis looks like to help you move beyond high-level policy review into technical verification.
Step 1: Framework Selection and Scoping
You must define the boundaries. Are you assessing the entire enterprise or just the Cardholder Data Environment (CDE) for a PCI DSS gap analysis? Are you looking at HIPAA compliance gaps across all clinics or just the main hospital?
Step 2: The "Design vs. Operating Effectiveness" Test
This is where most internal reviews fail.
- Design Effectiveness: Do you have a policy that says you patch systems every 30 days? (Paperwork check).
- Operating Effectiveness: Do you actually patch systems every 30 days? (Technical evidence check).
A true gap analysis pulls the logs, interviews the system administrators, and tests the evidence. It looks for compliance risk exposure in day-to-day operations, not the theory of the handbook.
Step 3: Risk Ranking and Remediation Roadmap
Not all gaps are the same. A missing policy document is a gap; a firewall allowing open RDP access to the internet is an emergency. The output of the analysis must be a prioritized roadmap that helps the CISO and CFO allocate resources to the highest risks first.
The Role of a vCISO: Gap-Analysis Compliance Officer
This is where the role of the CISO becomes indispensable to the Compliance Officer. For small businesses, however, a full-time CISO isn’t always practical or in the budget. That’s where a virtual CISO (vCISO) steps in, delivering the same strategic security leadership without the enterprise-level cost.
Interpreting regulatory compliance gaps takes both legal insight and technical depth. A vCISO bridges that divide. They turn the “legalese” of subpoenas and framework mandates into the technical requirements (i.e., server configurations, encryption standards, access controls) that make compliance work in practice.
How to Turn Your Anxiety into Audit Readiness
Skipping a compliance gap analysis means you willingly run your business with blind spots that could be devastating. If you only check controls once a year, you leave months of exposure unmonitored, and that exposure usually costs far more than staying compliant ever will. Mature organizations understand this, which is why they follow a consistent, rigorous assessment cadence. But you don’t have to shoulder that burden alone.
At CompassMSP, we don’t just hand you a list of problems. Our internal audit preparation works like a dress rehearsal. With guidance from our vCISO advisors, we uncover the skeletons in the closet before the auditor does, giving you the time and clarity to fix them.
Contact Compass MSP to get ahead of your next audit. Our vCISO advisors will help you find and fix compliance gaps before they become costly problems.
Answers to the Questions Every Compliance Officer Is Asking
-
What is the difference between a risk assessment and a compliance gap analysis?
While related, they have different goals. A compliance gap analysis compares your current controls specifically against the requirements of a standard (like HIPAA or SOC 2) to see where you fall short. A risk assessment identifies threats and vulnerabilities to your specific business assets, regardless of whether a regulation mentions them. You need both for total risk management compliance.
-
How often should we conduct a compliance gap assessment?
At a minimum, you should conduct a formal gap analysis annually. However, you must also trigger an analysis whenever there is a significant change in the business environment, such as adopting new software, migrating to the cloud, or when a regulation is updated (e.g., PCI DSS v4.0).
-
Can we perform a compliance gap analysis internally?
You can, but it carries risk. Internal teams often have "operational blindness,” where they see what they expect to see. They may also hesitate to report deep regulatory compliance gaps for fear of political fallout. Using a neutral third party, like a vCISO or external auditor, ensures an objective, evidence-based view of your compliance audit readiness.
-
What are the most common HIPAA compliance gaps found in small businesses?
Insurers now ask detailed questions about your security controls. A gap analysis provides the evidence to answer these questions accurately. It prevents the nightmare scenario where a claim is denied because the insurer determines you misrepresented your security posture on the application.
-
What is involved in a SOC 2 readiness assessment?
A SOC 2 readiness assessment is essentially a gap analysis for the Trust Services Criteria (Security, Availability, Processing Integrity, Confidentiality, and Privacy). It involves reviewing policies, interviewing staff, and gathering evidence to ensure that when the CPA firm arrives for the actual audit, the controls are operating effectively.
-
Does a gap analysis guarantee we will pass an audit?
No analysis can offer a 100% guarantee, as auditors act with their own discretion. However, a rigorous compliance gap analysis drastically reduces the probability of failure. It ensures there are no surprises and that you have a remediation plan and explanation for any minor issues that remain, which auditors respect.
-
How long does a typical compliance gap assessment take?
The timeline varies by organization size and complexity. For a small business, it might take 2-3 weeks. For a mid-sized company with multiple locations and complex data flows, it can take 4-8 weeks to fully interview staff, review configurations, and produce the compliance audit readiness report.
-
What happens if we find a major gap that we can't afford to fix immediately?
This is common. The key is to document it. Create a Plan of Action and Milestones (POAM). Acknowledge the risk, document a temporary mitigation (workaround), and set a date for the permanent fix. Auditors often accept a well-documented plan, whereas they will punish "willful ignorance" of the gap.