How to Identify a Phishing Email (with 3 Examples)
Phishing attacks are on the rise, especially since the pivot to remote work during the COVID-19 pandemic. The FBI’s Internet Crime Complaint Center (IC3) received 241,342 phishing complaints in 2020, more than twice the 114,707 it logged in 2019.
In 2021, phishing attacks continued to skyrocket off the charts.
While we are still waiting on the official FBI’s 2021 report, other reports are grim. Verizon’s 2021 Data Breach Investigations Report notes that phishing contributed to 36% of data breaches.
How familiar are you with this hacking tactic?
Chances are that you’ve found a phishing email in your inbox before. They are becoming more common and trickier to spot!
Today, we’re going to show you how to identify a phishing email and what to do once that phishing email is in your inbox. But first, let’s cover the basics of phishing attacks.
What is Phishing?
Fishing is the art of dangling bait to catch a meal.
Phishing is the art of dangling bait to catch someone’s personal information. Phishers will impersonate friends, families, companies, or authorities. Sometimes a phishing message looks like it comes from a trusted sender, like a bank. While under this guise, the phisher dangles offers or threats to attract attention.
When someone takes the bait, the phisher harvests their information or tricks them into a deceptive action. A phisher’s goal is to steal money and data — or get you to download infectious malware.
How does Phishing Work?
Phishing starts with a deceitful email, where the attacker tries to lure a victim. The email engages you, asking you to click on a link or download an attached document. The bait includes things like financial incentives, job offers, or missed payments.
A phishing email often includes bad links. Once the victim clicks on a phishing link, it takes them to the phisher’s website (which can be nearly identical to the real thing!). From there, the hacker will often capture the victim’s confidential information.
In other cases, the victim will open a malicious email attachment. This attachment then downloads malware onto the target’s computer.
3 Common Types of Phishing Attacks
Deceptive Phishing
Deceptive phishing is the most common type of phishing attack. This type is where an attacker steals confidential information from the victims. Using the stolen data, the attacker uses it to loot money or launch other attacks.
Spear Phishing
Spear phishing targets specific individuals instead of casting a wider net. Attackers often research their victims on social media. In turn, the attacker customizes their communications to appear more authentic.
Whaling
Whaling is when an attacker goes after a high-profile target, such as a CEO. These attackers often spend considerable time profiling their target to steal login credentials. Whaling can be extremely dangerous for businesses because executives often have access to greater company data.
How to Identify a Phishing Email?
In the phisher-infested Wild, Wild Net, you can’t let anyone lead you on!
Plain old skepticism is your best defense against phishing. Phishers want you to act without questioning what they’re telling you. That’s because their stories usually can’t hold up to closer inspection.
Like a good detective, you must be hyper-aware. Don’t take things at face value. Instead, it would be best if you looked over every email with a fine-tooth comb before replying or clicking a link.
Here are the telling signs that you are dealing with a phishing email:
Sender’s Email Address
The first question you should be asking yourself is: does the email address look fishy?
For example, let’s say you get an email saying it is from your bank, but the email address is strange. The address is YourBank@hotmail.com. That should be a red flag. The sender’s email, especially from a bank, should not use a public account, like Hotmail, Gmail, or Yahoo.
Incorrect URLs
Hackers use fake sites to steal your information. Before you click on an email’s URL, you need to ensure that the URL takes you to a legitimate site.
How do you find that out? If you’re on a computer, hover the mouse over the link. Once you do that, you’ll see a preview of the link in the status bar. The status bar is at the bottom left-hand corner.
For example, let’s say you get an email from “Target”. The URL in the email should take you to Target.com. You should not follow that link if you see something other than Target.com in the status bar.
Nosy Requests
Odd requests are enormous red flags. Legitimate banks and other companies will never ask for personal credentials via email. You should be suspicious of all emails requesting your sensitive information.
Your Name (or Lack of Name)
Does the email in question use your name? Phishing emails will often address the receiver as a “valued customer” or similar.
Also, if your name is misspelled, proceed with caution. If this email is legitimate, that company will have the correct info on file.
Typos
Real businesses are serious about email. Legitimate messages usually do not have major spelling mistakes or poor grammar. Read your emails carefully. If something seems off, don’t click on anything.
Ask an expert
Ask an expert if you do not know whether an email is real or fake. If your company uses an IT service provider, call the help desk and leave the guesswork to the experts.
3 Examples of Phishing Emails
Hopefully, you now understand how to spot a phishing email but we’re going to hit that point home with the following examples.
Below are three common examples of phishing emails. Please, feel free to share this information with your colleagues. The more people know about phishing, the better off for everyone.
COVID-19 Related Attacks
COVID-19 phishing attacks are becoming increasingly common and they show no signs of stopping.
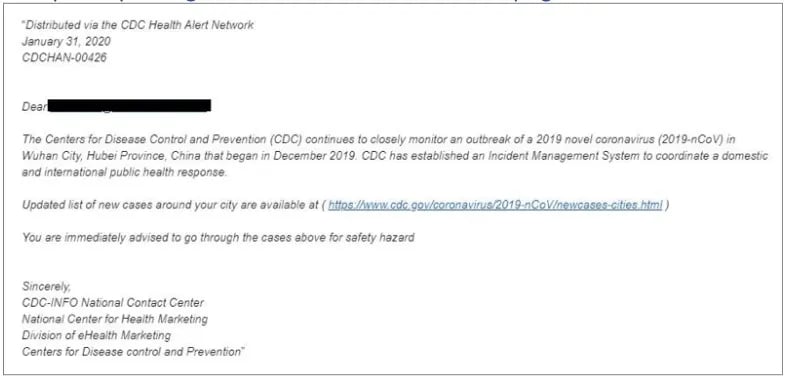
Here is an example of a phishing CDC alert:
In this example, the phishing email looks like it is from the US Centers for Disease Control and Prevention and it seems official, right?
But here’s the deal. That link does not go to the CDC government website.
Instead, it takes the end-user to a malicious website.
If we go back to our ‘tell-tale signs’ of a phishing email, we know to check the URL before clicking by hovering over the link. This action shows us a preview of the URL status.
In this example, the status bar wouldn’t show www.cdc.gov. It would show something suspicious like the following:
That is a red flag.
Tech Support Scams
Online retailers and services use email to communicate security updates to their customers. For example, they’ll message customers when they detect unusual activity.
Naturally, cybercriminals in the Wild, Wild Net are using this to their advantage.
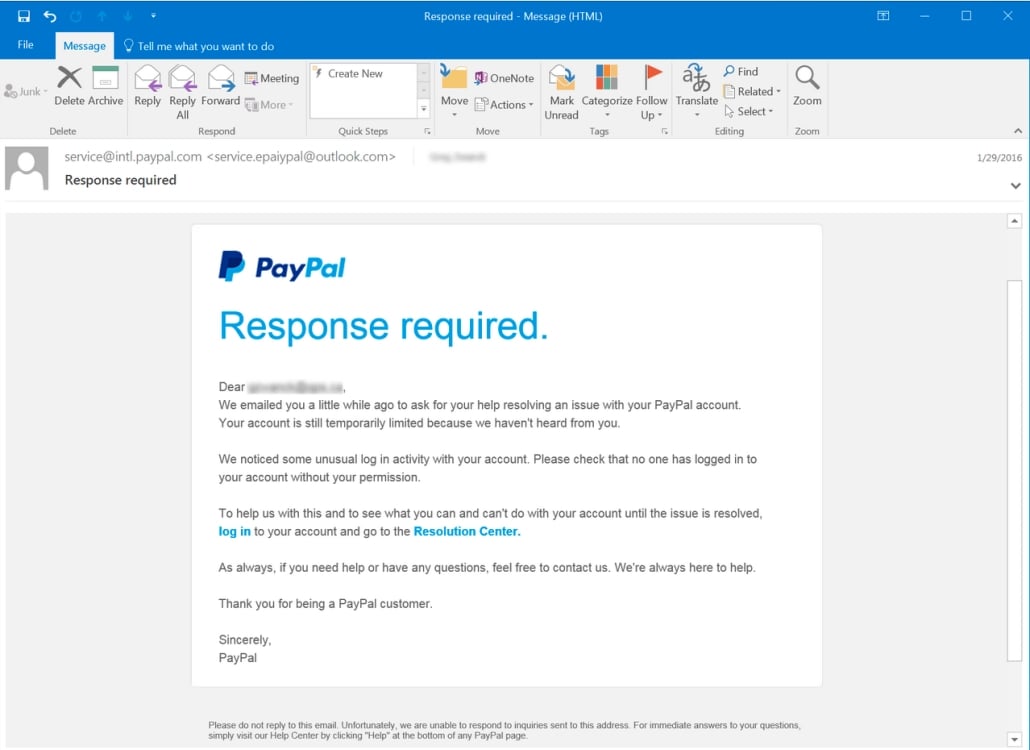
Take this example of a Fake PayPal security notice into consideration:
The first Red Flag in this example is the sender’s email address. An official PayPal email would not come from an Outlook account. Instead, it would come from PayPal.com.
Second, the wording in this email seems off. Why does PayPal need your help? Not to mention, the sentences are not grammatically correct.
Lastly, if you hover over the links, you’d likely catch that this is a phishing email. That’s because those links aren’t going to take you to PayPal.com.
Delivery Message Scams
Everyone loves getting packages! And cybercriminals love to exploit this fact.
Delivery phishing emails often entice you by sharing your package is on its way or that a package delivery was unsuccessful. It’s tricky to spot delivery scams. That’s because it is not uncommon to get an email from FedEx or UPS.
We expect to receive a delivery or tracking email when we order something online. It’s second nature at this point.
So, can you spot what is off in this “UPS” email?
While the graphics seem legitimate, they don’t quite add up. The message is about tracking a parcel, but the header graphic says, ‘UPS Billing Center’. Those are two separate departments.
But the even more obvious red flag is the sender email. That email address is not a UPS email account. Nice try, phisher!
What to Do if You Received a Phishing email?
Let’s say you just received a phishing email. And you realized it was a phishing email almost immediately. Now what?
First, nothing infects your computer if you don’t click on any links or respond. So, make sure you don’t click on anything.
If your company uses a managed service provider for IT, give your support desk a call. Explain that you received a phishing email and follow their protocols to handle it.
If you received the phishing email on a personal email account, the next step is to mark the sender as Junk or Spam.
You won’t want to get any more emails from the phisher who sent this one. Mark it as spam or junk, and your email provider will block any further mail from that address.
Finally, you should delete the email. Usually, this sends it to the recycle bin or deleted items folder, so remove it from there. There’s no need to keep it after you report it.
And now you can breathe a sigh of relief because you avoided a cyberattack. Nice!
Final Thoughts
Our digital world has its fill of cybercriminals. But if you continue your cybersecurity awareness training, you’ll be two steps ahead of them.
And when it comes to phishing attacks, user error opens the floodgates.
Stay vigilant!
Top Posts